- The paper presents a comprehensive taxonomy of Solana smart contract vulnerabilities and highlights key architectural differences with Ethereum.
- The study employs empirical data, including attack statistics and GitHub metrics, to quantify the disparity in available security tools.
- The paper underscores practical implications for improved security through enhanced tool integration, formal verification, and better developer education.
Vulnerabilities and Security Analysis in Solana Smart Contracts
Introduction
This paper presents a systematic investigation into the vulnerabilities and security concerns inherent in Solana smart contracts, contrasting the Solana ecosystem with Ethereum and providing a detailed analysis of available security tools, attack vectors, and mitigation strategies. The authors emphasize the unique architectural choices of Solana—such as its use of Rust and SBF bytecode—and the implications these have for smart contract security. The work is grounded in empirical data, including attack statistics and tool availability, and offers a technical taxonomy of vulnerabilities and analysis methodologies.
Comparative Ecosystem Analysis
The Solana ecosystem is characterized by a smaller but growing set of security analysis tools compared to Ethereum. The paper quantifies this disparity, noting 113 Ethereum-focused tools versus 12 for Solana, with an additional 13 supporting multiple platforms. This reflects Ethereum's maturity and broader adoption, as well as the relative nascency of Solana's developer and security communities.
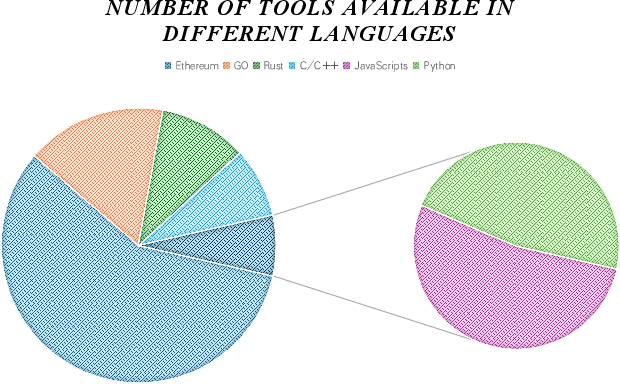
Figure 1: Number of Tools Available in Different Languages.
The analysis of GitHub metrics (issues and stars) further corroborates Ethereum's dominance in terms of community engagement and tool diversity. Solana's reliance on Rust introduces both opportunities and challenges: while Rust's safety guarantees mitigate certain classes of vulnerabilities (e.g., memory safety), the ecosystem lacks the breadth of specialized and comprehensive analysis tools found in Ethereum.
Taxonomy of Vulnerabilities
The paper provides a granular breakdown of vulnerability classes in Solana smart contracts, with detailed code examples and attack scenarios:
Lack of Check
- Signer Check: Absence of signature verification enables unauthorized administrative changes.
- Ownership Check: Failure to validate account ownership allows attackers to forge accounts and redirect funds.
- Rent-Exemption Check: Insufficient SOL balance can lead to account eviction and loss of state.
Conflation
- Account Type Confusion: Inadequate validation of account types and data formats can result in logic errors and security breaches.
- Cross-Instance Re-initialization: Shared state across contract instances enables attackers to bypass control flow and manipulate contract state.
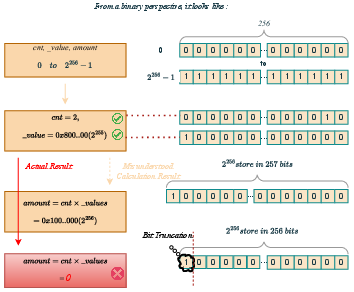
Calculation Errors
Unsafe Code
- Unsafe Rust Usage: Use of unsafe blocks can reintroduce memory corruption vulnerabilities.
- Outdated Dependencies: Stale libraries may harbor known exploits, necessitating regular audits.
Logic Vulnerabilities
- Sandwich Attacks: Exploitation of transaction ordering in AMM protocols for front-running and price manipulation.
- Oracle Attacks: Manipulation of external data sources to distort contract logic, with flash loans as a notable subclass.
Off-chain Factors
- Key Leakage: Weak entropy in key generation or poor key management practices can result in catastrophic asset loss.
- Promotion Software Hacking: Compromised social media channels can be leveraged for phishing and misinformation.
Security Analysis Methodologies
The paper categorizes security analysis tools into static, dynamic, and symbolic analysis, detailing their operational principles and limitations:
Static Analysis
Static analysis inspects source or bytecode without execution, employing techniques such as AST construction, control/data flow analysis, model checking, and theorem proving. Specialized tools (e.g., Blockworks Checked Math) offer high accuracy for domain-specific issues, while comprehensive tools (e.g., Kudelski Semgrep) provide broader coverage at the expense of precision.
Dynamic Analysis
Dynamic analysis involves runtime monitoring, with fuzz testing and dynamic taint analysis as primary techniques. Fuzzing iteratively mutates inputs to trigger exceptions, while taint analysis tracks the propagation of untrusted data. Both methods are constrained by path coverage and may miss subtle logic flaws.
Symbolic Execution
Symbolic execution explores program paths by treating inputs as symbolic variables, generating path predicates to identify hard-to-reach states. Static symbolic execution is limited by external calls and path explosion, while dynamic symbolic execution can invert branch conditions to discover new vulnerabilities. Hybrid approaches (e.g., Mythril) combine symbolic execution with SMT solvers and taint analysis for improved coverage.
Implications and Future Directions
The paper underscores the need for enhanced accuracy and usability in Solana security analysis tools. The integration of LLMs (e.g., GPT-4.5) is identified as a promising avenue for automated vulnerability detection and remediation, though methodological limitations remain. Usability is a critical bottleneck, with many tools lacking robust packaging and user interfaces. The authors advocate for open-source collaboration and the adaptation of Solidity-based analysis techniques to Solana, potentially facilitated by EVM compatibility layers such as Neon.
Theoretical implications include the necessity of formal verification and compositional reasoning in smart contract development, given the increasing complexity and financial stakes. Practically, the paper calls for improved developer education, rigorous auditing practices, and the adoption of best practices in key management and dependency hygiene.
Conclusion
This work provides a comprehensive technical survey of Solana smart contract vulnerabilities and the current landscape of security analysis tools. The comparative analysis with Ethereum highlights both the strengths and deficiencies of the Solana ecosystem. The taxonomy of vulnerabilities and detailed discussion of analysis methodologies offer actionable insights for researchers and practitioners. Future research should focus on toolchain integration, AI-assisted analysis, and the development of standardized security frameworks to advance the reliability and trustworthiness of Solana smart contracts.