The Treasury Proof Ledger: A Cryptographic Framework for Accountable Bitcoin Treasuries (2512.03765v1)
Abstract: Public companies and institutional investors that hold Bitcoin face increasing pressure to show solvency, manage risk, and satisfy regulatory expectations without exposing internal wallet structures or trading strategies. This paper introduces the Treasury Proof Ledger (TPL), a Bitcoin-anchored logging framework for multi-domain Bitcoin treasuries that treats on-chain and off-chain exposures as a conserved state machine with an explicit fee sink. A TPL instance records proof-of-reserves snapshots, proof-of-transit receipts for movements between domains, and policy metadata, and it supports restricted views based on stakeholder permissions. We define an idealised TPL model, represent Bitcoin treasuries as multi-domain exposure vectors, and give deployment-level security notions including exposure soundness, policy completeness, non-equivocation, and privacy-compatible policy views. We then outline how practical, restricted forms of these guarantees can be achieved by combining standard proof-of-reserves and proof-of-transit techniques with hash-based commitments anchored on Bitcoin. The results are existence-type statements: they show which guarantees are achievable once economic and governance assumptions are set, without claiming that any current system already provides them. A stylised corporate-treasury example illustrates how TPL could support responsible transparency policies and future cross-institution checks consistent with Bitcoin's fixed monetary supply.
Sponsor
Paper Prompts
Sign up for free to create and run prompts on this paper using GPT-5.
Top Community Prompts
Explain it Like I'm 14
A simple explanation of “The Treasury Proof Ledger: A Cryptographic Framework for Accountable Bitcoin Treasuries”
1. What is this paper about?
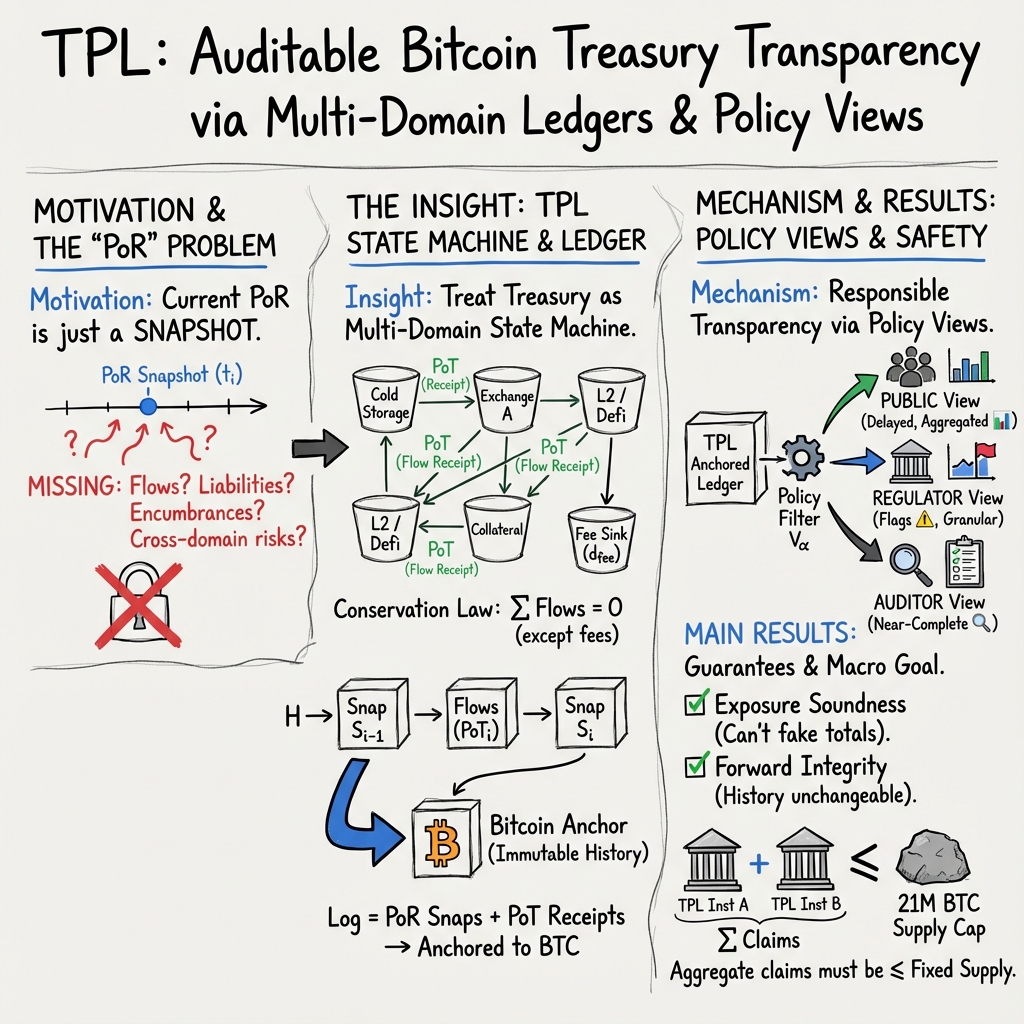
This paper introduces a new way for companies that hold Bitcoin to be transparent about what they own—without revealing sensitive details that could put them at risk. The authors call their system the Treasury Proof Ledger (TPL). Think of TPL as a secure, tamper-proof diary that records a company’s Bitcoin-related activities across many areas (like wallets, exchanges, loans, and derivatives), then “stamps” those records onto the Bitcoin blockchain so no one can quietly change them later.
2. What questions are they trying to answer?
The paper focuses on simple but important questions:
- How can a company show it really has the Bitcoin it claims, across different places and products (not just one wallet or one exchange)?
- How can it do this regularly over time, not just once?
- How can it prove movements of Bitcoin between different parts of its business are real and accounted for?
- How can it share just the right amount of information with different people (investors, auditors, regulators) without exposing sensitive details?
- How can all these records work together so outside observers can trust them?
3. How does their approach work?
The authors design TPL using everyday ideas:
- Multiple “jars” for money:
- Imagine a company’s Bitcoin is spread across many labeled jars: “cold wallets,” “custodian,” “exchange,” “loans,” “derivatives,” and a special “fee jar.” Bitcoin can move from one jar to another. The total across all jars (except the fee jar) stays consistent unless Bitcoin truly leaves (like paying a network fee), which is recorded in the fee jar. This is like a conservation rule for value: if you move 5 BTC from jar A to jar B, the total doesn’t change—just the distribution.
- Proof-of-Reserves (PoR) snapshots:
- These are like inventory checks. A company (or its partners) cryptographically proves it really controls certain Bitcoin, without revealing all addresses or private details. This answers “Do they actually have it?”
- Proof-of-Transit (PoT) receipts:
- These are like stamped receipts when value moves between jars. Each transfer gets a signed, time-stamped record that’s chained to the previous ones, building a trackable chain of custody. This answers “Did the value actually move the way they say?”
- A hash-chained, anchored ledger:
- Picture each page of the diary having a unique “fingerprint” (a hash) that depends on its content and the previous page. If anyone tries to change a past page, the fingerprints stop matching. Then, the company takes a summary of this diary and anchors it onto Bitcoin (by including the fingerprint in a Bitcoin transaction). Once anchored and confirmed, it’s extremely hard to deny or rewrite history.
- Policy-based views:
- Different people see different slices of the ledger. Investors might see high-level totals and changes. Auditors get more detail. Regulators may see even more. Policies are like filters that decide who sees what—so transparency doesn’t leak sensitive trading strategies or operational details.
4. What did they find, and why is it important?
The paper doesn’t just propose an idea—it also shows what can be guaranteed if the system is used properly and at least one party per “jar” is honest (for example, an honest auditor, an honest anchoring key, or an honest proof provider):
- Conservation of value across domains:
- The “jars” system follows a clear rule: value moving between jars balances out, and fees go into a fee jar. This helps detect cheating like counting the same Bitcoin twice.
- No two conflicting histories (non-equivocation):
- Because the ledger pages are hash-chained and anchored to Bitcoin, a company can’t present one version of history to investors and a different one to regulators without getting caught. That’s strong accountability.
- Correct filtered views:
- If the policy says a certain kind of event must be shown to investors, and the system is used honestly, the view they get will match what’s in the anchored ledger. Views can be re-checked by others.
- Restricted exposure soundness and privacy:
- The authors prove “existence-style” guarantees for certain realistic cases:
- They show exposure soundness in a restricted setting (closed set of jars and faithful policies) using standard tools like PoR and PoT.
- They also prove a limited privacy result for a specific “public investor” case.
- They are clear about limits: they do not claim to solve privacy for every possible policy or observer. Those are left for future work.
Why this matters:
- Today’s “proof-of-reserves” checks are often one-time and narrow (e.g., one exchange, one moment). TPL generalizes this to a full, ongoing, multi-part treasury with rules, receipts, and anchoring, built from standard cryptographic parts. It supports responsible transparency without broadcasting live wallet maps that could be dangerous.
5. Why does this matter, and what could it lead to?
TPL aims to be a practical foundation for how companies can be transparent about Bitcoin holdings in a way that:
- Protects their operations and strategies,
- Gives investors and auditors trustworthy records,
- Helps regulators get the information they need,
- Creates a clearer picture across the whole market.
A big future application the authors highlight is “supply-consistency” checks across many institutions. Because Bitcoin has a fixed cap of 21 million BTC, observers might someday use families of TPL logs to verify that total claimed holdings by funds, companies, and custodians don’t add up to more than what actually exists—helping prevent hidden double-counting or excessive rehypothecation.
The authors stress that:
- Their results depend on standard cryptography, Bitcoin anchoring assumptions, and a minimal “not everyone is colluding” condition.
- Their privacy proof is limited to specific public-investor settings.
- They’re not replacing accounting standards; they’re providing a cryptographic backbone that can support better audits and disclosures.
In short, TPL is a blueprint for a safer, smarter transparency system for Bitcoin treasuries—one that balances honesty with operational safety, uses widely understood cryptographic tools, and opens the door to stronger market-wide checks in the future.
Knowledge Gaps
Below is a single, actionable list of the paper’s unresolved knowledge gaps, limitations, and open questions. Each item is framed to guide future research and implementation work.
- Formalize and prove exposure soundness for open domain sets that include external counterparties, intermittent coverage, and dynamic domain membership, beyond the current “closed set under faithful policy” restriction.
- Develop a general privacy framework and proofs for richer, stateful policies and heterogeneous observers (auditors, regulators, counterparties), including leakage functions that capture timing, amounts, and cross-domain correlations.
- Specify and verify policy completeness for expressive, stateful policies (e.g., thresholded, risk-based, or time-dependent disclosure rules), rather than only deterministic, stateless or simple history-revealing policies.
- Design and analyze mechanisms to detect domain incompleteness (missing or shadow domains) and intentional scope arbitrage across subsidiaries or related entities.
- Provide concrete, standardized mappings from complex instruments (derivatives, collateralized lending, structured products) to BTC-equivalent exposures, including treatment of encumbrances, netting, and optionality.
- Integrate liabilities and encumbrances modeling into the formal state machine with clear primitives and proofs, rather than relying on governance metadata alone.
- Construct and evaluate concrete PoR/PoT primitives and interoperability profiles suitable for custodians, exchanges, L2s, and prime brokers (including APIs, attestations, and proof formats), instead of assuming them as black-box primitives.
- Establish robust evidence provenance for off-chain attestations (exchange APIs, custodian statements) via TEEs, remote attestation, or auditor-signed artifacts, and prove end-to-end soundness incorporating these trust anchors.
- Quantify and harden against inference attacks from timestamps, anchoring cadence, and cross-correlation with public on-chain activity (e.g., develop measurable privacy budgets or differential privacy-style leakage bounds).
- Define correction semantics for operational errors and restatements within an append-only ledger (how to log corrections, supersessions, and reconciliations while preserving forward integrity and auditable history).
- Analyze partial-collusion resilience: formally characterize which subsets of roles (treasurer, PoR/PoT providers, anchoring keys, auditors) can collude without breaking exposure soundness, and design MPC or threshold anchoring protocols to enforce non-collusion.
- Extend non-equivocation guarantees to policy views under complex, possibly stateful policies, ensuring that no observer can be fed a policy-specific but inconsistent view that is nonetheless anchor-consistent.
- Provide performance, scalability, and cost evaluations (throughput, storage growth, anchoring fees, latency bounds) for large treasuries and multi-institution deployments; include empirical measurements and stress tests.
- Model liveness failures and recovery (network partitions, anchoring delays, provider outages) and define verifiable recovery procedures, backlog handling, and out-of-order event reconciliation.
- Formalize cross-layer exposure tracking for Lightning channels, rollups, and commit chains, including proofs of state correctness and channel-level encumbrance or liquidity constraints.
- Address reorg and soft-fork risks by specifying how TPL handles anchoring finality thresholds, chain upgrades (Taproot, future opcodes), and validation of legacy commitments under protocol changes.
- Specify a standardized, machine-checkable policy language with versioning, compositionality, conflict resolution, and formal semantics, and provide a compiler or verifier toolchain for reproducibility.
- Develop cross-entity consolidation rules (intercompany transfers, beneficial ownership, subsidiary hierarchies) and formal proofs that prevent double-counting or omission in group-level exposure views.
- Propose a concrete macroprudential “supply-consistency” protocol: define coverage assumptions, attestation aggregation, deduplication, and statistical methods to bound total claims vs. the 21M cap, and prove soundness under partial participation.
- Explore extensions beyond BTC-only exposures to multi-asset treasuries and cross-asset instruments, including how to maintain conservation laws and privacy when assets are not natively auditable on Bitcoin.
- Define and validate reconciliation tolerances (rounding, dust, consolidation, fee estimation) and their effect on conservation proofs and exposure soundness at operational scales.
- Establish governance and regulatory integration: articulate audit standards, IFRS/GAAP alignment, legal semantics of PoT receipts, dispute resolution frameworks, and regulator-operated anchoring or monitoring roles.
- Specify key management procedures (rotation, compromise response, multi-party control) and prove non-repudiation and continuity of commitments across key lifecycle events.
- Provide open-source verifier tooling and light-client protocols for public observers, including standardized artifacts, reproducible builds, and reference datasets to evaluate adoption feasibility.
- Characterize adversarial scheduling within admissible bounds and define observable signals or watchdog protocols that detect and escalate liveness violations indicative of operational failure.
- Evaluate the trade-offs between “responsible transparency” and market impact (front-running, strategic leakage), and design policies or cryptographic mitigations that minimize exploitable disclosures without undermining accountability.
Glossary
- Accountable logging: Cryptographic logging discipline that produces append-only, verifiable records to enable accountability. "transparency-log and accountable-logging frameworks"
- Anchoring: Publishing cryptographic commitments on Bitcoin to make logs tamper-evident and globally verifiable. "TPL commitments are anchored to Bitcoin at least once every $\Delta_{\mathsf{anchor}$."
- Anchoring keys: Keys that authorize publishing TPL commitments to the Bitcoin blockchain. "the keys used to anchor TPL commitments to Bitcoin"
- Append-only ledger: A log structure that permits only appends (no edits), enabling verifiable history. "Bitcoin is modelled as an append-only ledger with -confirmation finality"
- Certificate Transparency (CT): A system of public, append-only logs used to audit certificate issuance. "Transparency log systems such as Certificate Transparency publish append-only, publicly auditable logs"
- Collision resistance: Property of a hash function making it computationally infeasible to find distinct inputs that hash to the same output. "collision-resistance"
- Conservation law: An invariant stating that total BTC-equivalent exposure across domains is conserved modulo fees. "a conservation law for Bitcoin exposures across domains (Theorem~\ref{thm:conservation});"
- DAPOL (Distributed Auditing Proofs of Liabilities): A PoR variant enabling partitioned audits and light-client verification. "Distributed Auditing Proofs of Liabilities (DAPOL), enabling audits over partitioned customer sets and light-client friendly verification"
- Encumbrances: Legal or contractual claims restricting asset use (e.g., collateral pledges). "do not model encumbrances or cross-domain flows"
- EUF-CMA: Existential unforgeability under chosen-message attack, a standard security notion for signatures. "EUF-CMA"
- Exposure soundness: Assurance that reported treasury exposures are not overstated beyond reality under stated assumptions. "exposure soundness"
- Exposure vector: A structured, multi-domain vector of BTC-equivalent positions tracked by the treasury state machine. "explicit multi-domain exposure vector"
- Fee sink: A dedicated domain that accumulates irrecoverable outflows like network fees. "explicit fee sink"
- Forward integrity: Guarantee that once records are logged, later compromise cannot alter past entries undetectably. "Forward integrity and auditability."
- Forward-secure logging: Logging where keys evolve over time so past entries remain secure even if current keys are compromised. "forward-secure logging (PoT)"
- Hash-chained commitments: Commitments linked via hashes so any change breaks the chain and becomes detectable. "hash-chained commitments"
- k-confirmation finality: The assumption that Bitcoin transactions are effectively immutable after k confirmations. "Bitcoin is modelled as an append-only ledger with -confirmation finality"
- Leakage function: A formal specification of exactly what information a policy-authorized observer may learn. "leakage functions and simulation-based privacy"
- Light-client: A client that verifies proofs with minimal data and computation, without storing the full blockchain. "light-client friendly verification"
- Liveness bounds: Assumed time limits within which events must be processed, snapshotted, and anchored. "subject to the liveness bounds below."
- Macroprudential supply-consistency checks: Cross-institutional verifications that aggregate claims do not exceed Bitcoin’s fixed supply. "macroprudential supply-consistency checks against Bitcoin's fixed monetary cap"
- Minimal non-collusion: Assumption that at least one key role per domain behaves honestly, preventing total fabrication. "Minimal non-collusion assumption."
- Non-equivocation: Inability to present two conflicting histories as valid to honest observers. "Non-equivocation"
- Non-repudiation: Property that prevents parties from plausibly denying logged and anchored events. "a forward-integrity and non-repudiation guarantee based on non-equivocation"
- Policy completeness: Guarantee that all events required by a disclosure policy eventually appear in the committed ledger. "policy completeness"
- Policy-based views: Stakeholder-specific projections of the ledger determined by declared disclosure policies. "policy-based views for different stakeholders."
- Proof-of-Reserves (PoR): Cryptographic attestations that assets (and sometimes liabilities) match claims, typically via UTXO proofs. "proof-of-reserves (PoR)"
- Proof-of-Transit (PoT): Hash-chained receipts documenting transfers between treasury domains. "Proof-of-Transit (PoT)"
- Proof-of-Transit Timestamping (PoTT): A transport-layer receipt scheme producing signed, timestamped chains of custody. "Proof-of-Transit Timestamping (PoTT)"
- PPT (Probabilistic Polynomial Time): Class of efficient randomized algorithms used to formalize cryptographic parties and adversaries. "All probabilistic algorithms are modelled as PPT (probabilistic polynomial time)"
- Rehypothecation: Reusing pledged assets, potentially causing multiple claims on the same BTC. "hidden rehypothecation"
- Simulation-based privacy: Privacy defined via a simulator that reproduces observer views given only the allowed leakage. "we prove a simulation-based theorem only for a specific public-investor leakage profile"
- Stateless policies: Policies whose outputs depend only on current inputs, not on internal mutable state. "deterministic, stateless policies"
- Transparency logs: Public append-only logs used to make misbehavior detectable via consistency checks. "Transparency log systems such as Certificate Transparency publish append-only, publicly auditable logs"
- Treasury Proof Ledger (TPL): A Bitcoin-anchored framework logging multi-domain exposures with policy-based views and integrity guarantees. "We propose the Treasury Proof Ledger (TPL)"
- UTXO (Unspent Transaction Output): Bitcoin’s model where balances are sets of unspent outputs rather than account totals. "a set of on-chain UTXOs"
- Witness-indistinguishable argument systems: Proof systems where different valid witnesses are indistinguishable to the verifier. "witness-indistinguishable argument systems"
- zk-SNARK: Succinct, non-interactive zero-knowledge proof system used to prove complex relations efficiently. "a general-purpose zk-SNARK encoding the PoR and PoT validity predicates together with the conservation law"
Practical Applications
Immediate Applications
Below are deployable, concrete use cases that can be implemented with the paper’s Treasury Proof Ledger (TPL) model and the standard building blocks it composes (proof-of-reserves, proof-of-transit logging, hash-chained commitments anchored to Bitcoin).
- Corporate Bitcoin Treasury Accountability Stack (Finance, Enterprise Software)
- Description: Stand up a single-company TPL instance to log multi-domain exposures (custody, exchanges, derivatives, Lightning, fee sink), anchor snapshots to Bitcoin, and publish policy-defined views for investors, auditors, and regulators. Resolves transparency-versus-privacy tension without publicly doxxing operational wallet maps.
- Potential tools/products/workflows: TPL Node (ledger + hash-chain + anchoring), Policy View Engine (observer-specific views), Anchoring Orchestrator (k-confirmation monitoring), Custodian/Exchange Connectors (PoR ingestion), Auditor CLI (re-verification and sampling).
- Assumptions/Dependencies: Minimal non-collusion per domain; k-confirmation finality; availability of PoR statements from service providers; faithful policy-to-domain mapping; liveness bounds for event, snapshot, and anchoring cadence; governance clarity on BTC-equivalent exposure mapping for complex instruments.
- Auditor Replayable Evidence Trail (Audit/Assurance)
- Description: Use TPL’s non-equivocating, Bitcoin-anchored log as forward-secure audit evidence; replay event timelines, reconcile domain flows, and tie audit samples to immutable anchors, producing reproducible workpapers aligned with IFRS/GAAP exposure assertions.
- Potential tools/products/workflows: Auditor Console (timeline replay, sampling), Re-verification CLI (anchor cross-checks), PoR Ingestion Module (existence/control tests), Policy-to-Disclosure Checklist (completeness tests).
- Assumptions/Dependencies: Auditor independence; coverage of in-scope domains and encumbrances; restricted exposure-soundness holds for closed domain sets under faithful policies; mapping between BTC exposures and financial-statement presentation; cooperation from custodians/exchanges.
- Regulator Pilot: Responsible Treasury Disclosures (Policy/RegTech)
- Description: Run a supervisory pilot where regulated firms publish a standard public-investor view (e.g., “cold holdings + movements >1% of treasury”) with replayable anchors; regulators hold/oversee anchoring keys (e.g., via HSM/MPC) to bolster non-collusion.
- Potential tools/products/workflows: Regulator Portal (policy registry + view validation), Anchoring Key Custody (regulated HSM/MPC), Disclosure Policy Templates (deterministic, stateless policies).
- Assumptions/Dependencies: Minimal non-collusion enforced through key governance; privacy guarantees limited to the paper’s public-investor leakage profile; statutory acceptance of cryptographic evidencing; consistent liveness.
- Investor Relations and Market Data Feeds (Capital Markets, Media/Data)
- Description: Publish machine-readable, Bitcoin-anchored public-investor views; enable third-party data providers to ingest exposure snapshots, conservation checks, and fee-sink summaries as transparency signals for valuation and risk analytics.
- Potential tools/products/workflows: TPL Explorer (JSON/CSV feeds, API endpoints), Anchor Watcher (finality alerts), Coverage Labels (domains/policies in scope).
- Assumptions/Dependencies: Firms agree on disclosure policies and cadence; markets accept policy-limited leakage; stable anchoring schedule; domain coverage disclosed.
- Custodian/Exchange Client PoR Bundling (Crypto Custody/Exchanges)
- Description: Offer signed PoR snapshots and PoT receipts to corporate clients on a TPL-friendly schedule; reduce friction in treasury attestations and enable inter-domain movement justification.
- Potential tools/products/workflows: PoR API (existence/ownership attestations), PoT Receipt API (transfer digests), TPL Integration SDK (normalizing evidence formats).
- Assumptions/Dependencies: Provider adoption; accurate UTXO/exposure mapping; service-level liveness; at least one honest role per domain.
- Incident Response and Forensics (Security/IR)
- Description: Leverage non-equivocation and forward integrity to reconstruct tamper-evident timelines after security events; correlate fee-sink outflows and inter-domain transfers with anchored receipts for root-cause analysis.
- Potential tools/products/workflows: Forensic Replay and Diff Tool (event-by-event comparison), Anchor Consistency Checker (chain reorg detection), Evidence Export (auditor/regulator packages).
- Assumptions/Dependencies: TPL operated continuously pre-incident; events captured with sufficient metadata; Bitcoin anchors achieved with k-confirmations.
- Treasury Operations Risk Control (Enterprise Risk Management)
- Description: Internal dashboards verify conservation across domains, policy adherence (e.g., movement thresholds), and fee reconciliation; trigger alerts on missing receipts, stale snapshots, or policy violations.
- Potential tools/products/workflows: Conservation Monitor (exposure vector tracking), Policy Compliance Engine (threshold rules), Fee Sink Reconciler (network fee accounting).
- Assumptions/Dependencies: Domain completeness; deterministic policy definitions; timely connectors to service providers; clear exposure normalization rules.
- Academic Teaching and Lab Exercises (Education, Academia)
- Description: Use the TPL state machine and policy views to teach accountable logging, cryptographic audits, and treasury governance; run lab exercises on testnet anchors and simulated domains.
- Potential tools/products/workflows: TPL Simulator (event generation), Testnet Anchor Toolkit, Course Modules (state machine, conservation law, PoR/PoT composition).
- Assumptions/Dependencies: Open-source reference implementation; simplified policies; testnet Bitcoin availability.
- Counterparty Due Diligence for OTC Deals (Corporate Finance)
- Description: Share policy-defined views to evidence collateral or BTC capacity prior to OTC trades or structured financing; reduce information asymmetry while preserving operational privacy.
- Potential tools/products/workflows: Counterparty Verifier (view request + re-verification), Policy Negotiation Templates, Evidence Bundles (anchors + receipts).
- Assumptions/Dependencies: Legal agreements on accepted policy views; domains in scope for the deal; mutual trust in anchoring schedule and non-collusion.
Long-Term Applications
These use cases require further research, scaling, standard-setting, or ecosystem adoption beyond the paper’s current restricted guarantees (e.g., richer privacy, multi-institution exposure soundness, harmonized policies).
- Macroprudential Bitcoin Supply Consistency Network (Policy/Finance/Data)
- Description: Aggregate independently operated TPL instances across ETFs, corporates, custodians to compute lower bounds on BTC under management; watch for aggregate claims exceeding Bitcoin’s 21M cap.
- Potential tools/products/workflows: Supply Consistency Aggregator (cross-ledger reconciler), Monitor/Gossip Network (anchoring schedule consistency), Public Dashboard (coverage and bounds).
- Assumptions/Dependencies: Broad institutional adoption; harmonized policies and domain taxonomies; coverage disclosures; privacy-preserving aggregation methods; regulatory coordination.
- Zero-Knowledge Rich Privacy Views (Cryptography/Compliance)
- Description: Compile exposure soundness, conservation, and policy completeness into zk-proofs that hide wallet maps and sensitive flows while verifying treasury-wide claims.
- Potential tools/products/workflows: zkTPL Prover (SNARK circuits for PoR/PoT + conservation), zk Verifier (light-client friendly checks), Circuit Standards (auditable predicates).
- Assumptions/Dependencies: Efficient zk systems for large state; robust leakage modeling; regulator acceptance of zk attestations; formal privacy for richer policies.
- Standards and Accounting Integration (Standards/Accounting)
- Description: Develop IFRS/GAAP annexes and XBRL taxonomies for BTC-equivalent multi-domain exposures, encumbrances, and fee sinks; codify reconciliation tolerances and disclosure rules.
- Potential tools/products/workflows: XBRL TPL Taxonomy, ISA/ISAE Addenda (audit procedures), Policy Catalogue (industry-standard disclosure sets).
- Assumptions/Dependencies: Standard-setter buy-in; precise legal semantics for derivatives/encumbrances; cross-jurisdiction harmonization.
- Inter-institutional Non-Equivocation Watchers (Infrastructure)
- Description: A CT-like ecosystem of independent monitors that verify anchoring cadence, hash consistency, and view correctness across many treasuries; detect equivocation or omission at scale.
- Potential tools/products/workflows: Watcher Nodes (consistency checks), Gossip Protocols (ledger head exchange), Alerting/Slashing-like reputational mechanisms.
- Assumptions/Dependencies: Sufficiently decentralized monitors; public access to anchoring artifacts; standardized APIs.
- Insurance Underwriting and Operational Risk Scoring (Insurance)
- Description: Use TPL-derived metrics (policy adherence, exposure dispersion, fee-sink behavior, liveness) to price operational risk for BTC-heavy firms and set coverage terms.
- Potential tools/products/workflows: Risk Score Feeds, Underwriting Models (TPL indicators), Portfolio Benchmarks (cross-firm comparators).
- Assumptions/Dependencies: Historical datasets; validated linkage between TPL metrics and loss outcomes; monitor independence; avoidance of ecosystem-wide collusion.
- Automated Compliance Engines (RegTech)
- Description: A policy language that compiles supervisory constraints (movement thresholds, segregation, liquidity buffers) into machine-checkable TPL predicates with real-time alerts.
- Potential tools/products/workflows: Policy Compiler (to verifiable checks), Compliance Orchestrator (alerting + workflow), Evidence Vault (anchored artifacts).
- Assumptions/Dependencies: Expressive yet analyzable policy language; integration with AML/KYC and traditional systems; regulator-approved predicates.
- ETF Prospectus and NAV Attestation Pipelines (Asset Management)
- Description: Use TPL to support daily NAV attestations, movement justifications for authorized participants, and transparency modules for prospectus disclosures.
- Potential tools/products/workflows: NAV Attestation Pipeline (TPL + custodian PoR), AP Portal (view-based collateral checks), Audit Trail Export.
- Assumptions/Dependencies: Custodian/exchange API alignment; policy harmonization across fund complexes; acceptance by securities regulators.
- Layer-2 and Cross-Domain Extensions (Blockchain Infrastructure)
- Description: Extend TPL to Lightning, rollups, and commit chains; formalize exposures and finality assumptions across multiple substrates; anchor summaries to Bitcoin.
- Potential tools/products/workflows: L2 Domain Adapters (state commitments), Cross-Chain Anchoring Tools, Reconciliation Bridges (fee and exposure sinks).
- Assumptions/Dependencies: Reliable PoR/PoT equivalents on L2s; cross-domain finality guarantees; ecosystem standards for commit-chain evidence.
- Interplanetary PoTT/TPL (Space/Telecom)
- Description: Apply PoTT receipts across delay-tolerant relays (Earth–Moon–Mars) and anchor treasury events under long-latency assumptions; useful for space-based custody or communications research.
- Potential tools/products/workflows: Space Relay PoTT Stack, Delay-Tolerant Anchoring Schedules, Mission Audit Views.
- Assumptions/Dependencies: Space-grade networking/security; anchoring governance across jurisdictions; specialized liveness windows.
- Open-Source Explorer and Rating Methodologies (Media/Data)
- Description: Public explorers that score treasuries on policy completeness, exposure soundness, anchoring regularity, and conservation discipline; feed ratings to investors and analysts.
- Potential tools/products/workflows: TPL Explorer, Rating Methodology (transparent metrics), Data Partnerships (index providers).
- Assumptions/Dependencies: Community governance for metrics; transparent methodology; sufficient dataset coverage; resilience to gaming.
- TPL-as-a-Service (Software/SaaS)
- Description: Managed service offering TPL node operation, anchoring orchestration, multi-party HSM keys, and connectors; turnkey deployments for corporates and funds.
- Potential tools/products/workflows: Managed TPL Platform, HSM/MPC Anchoring, Compliance Support (policy templates).
- Assumptions/Dependencies: Vendor trust; secure multi-tenant isolation; SLAs for liveness and anchoring; external audit of the service.
- Retail Investor Due Diligence Apps (Daily Life, Fintech)
- Description: Mobile/web apps that let retail investors verify anchored public views of companies they own; alerts on missed anchors or policy deviations.
- Potential tools/products/workflows: Investor App (view re-verification), Notification Service (anchoring events), Portfolio Integration.
- Assumptions/Dependencies: Availability of public views; user education on policy scope; data-provider integration; reliable Bitcoin anchoring observation.
Collections
Sign up for free to add this paper to one or more collections.