Side Auth: Synthesizing Virtual Sensors for Authentication (2301.11745v1)
Abstract: While the embedded security research community aims to protect systems by reducing analog sensor side channels, our work argues that sensor side channels can be beneficial to defenders. This work introduces the general problem of synthesizing virtual sensors from existing circuits to authenticate physical sensors' measurands. We investigate how to apply this approach and present a preliminary analytical framework and definitions for sensor side channels. To illustrate the general concept, we provide a proof-of-concept case study to synthesize a virtual inertial measurement unit from a camera motion side channel. Our work also provides an example of applying this technique to protect facial recognition against silicon mask spoofing attacks. Finally, we discuss downstream problems of how to ensure that side channels benefit the defender, but not the adversary, during authentication.
Summary
- The paper proposes synthesizing virtual sensors from analog sensor side channels to enable robust multimodal authentication.
- It develops an analytical framework categorizing sensor side channels based on component separability and controllability.
- Evaluations using virtual IMUs achieved up to an 87.5% reduction in false positives for facial recognition systems.
SideAuth: Virtual Sensor Synthesis for Authentication
This paper introduces a novel paradigm shift in how analog sensor side channels are viewed and utilized, positing that instead of solely focusing on mitigating these channels, they can be harnessed for defensive purposes, specifically for authenticating sensor measurands (2301.11745). The core idea revolves around synthesizing virtual sensors from existing circuits to enable multimodal authentication, enhancing system security by leveraging the inherent physics of sensors.
Analytical Framework for Sensor Side Channels
The authors present an analytical framework for modeling analog sensor side channels, categorizing them based on their separability from intended signals and the controllability of their mitigation mechanisms. A sensor is modeled as a function that maps physical measurands to digital measurements:
m=f(sint,sside)
where m is the digital measurement, sint is the intended measurand, and sside represents the set of hidden variables leading to side channels. The framework defines a sensor side channel as a communication channel that allows secret information recovery using unintended sensor measurement components, violating the system's security expectations.
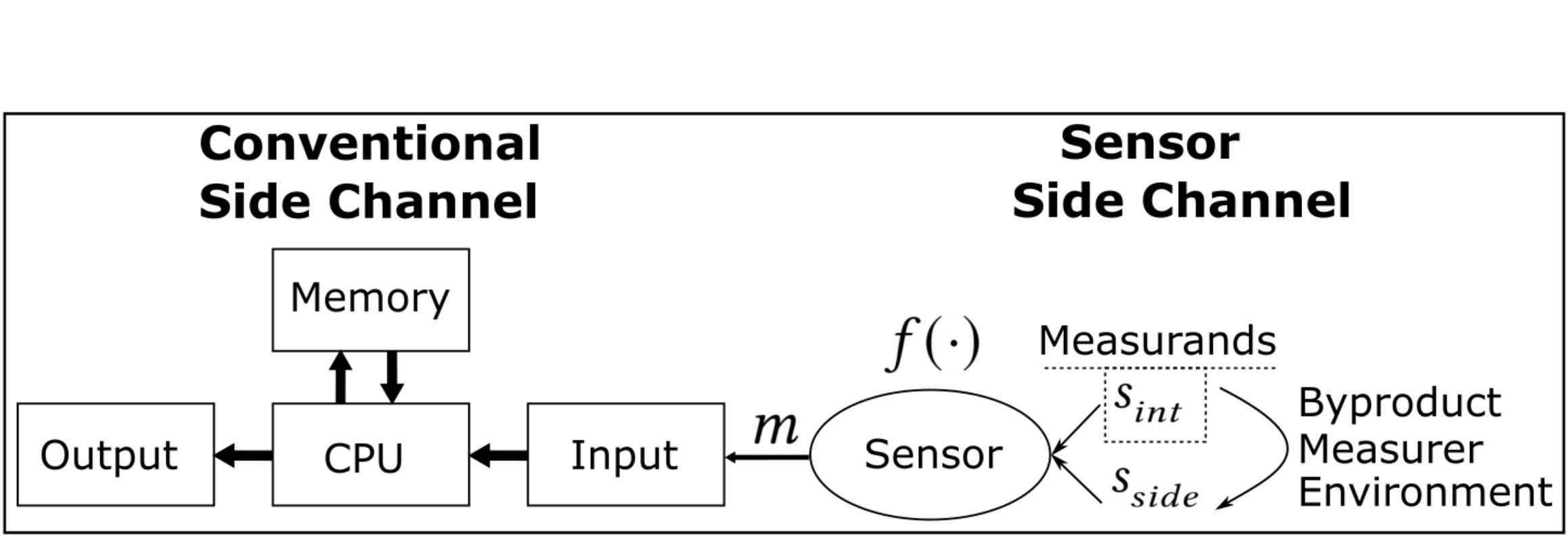
Figure 1: Sensor side channels measure the measurement processes, unlike conventional side channels that measure computation processes, allowing for verification of the authenticity of intended sensor measurands by examining byproducts, the measurer, and the environment.
The separability of unintended components from intended signals is crucial. Separable components allow mitigation through mechanisms like compensation, calibration, and noise reduction. A controllable sensor side channel is one where the unintended measurement component is separable and suppressible via an enable/disable mitigation mechanism. Examples include inseparable side channels like those exploited in Gyrophone attacks, separable but uncontrollable channels like temperature sensitivity in MEMS sensors, and controllable channels like video stabilization in cameras.
Virtual Sensor Synthesis and Measurand Authentication
The paper defines a virtual sensor as a function that maps sensor measurements to specific side channel components. The core problem is framed as a binary hypothesis test, comparing unimodal authentication (using only the physical sensor's measurand) against multimodal authentication (incorporating synthesized virtual sensors). The goal is to construct virtual sensor functions and a multimodal authentication system that achieves better performance, i.e., reduces the total error in measurand authentication.
The security properties of this approach lie in its ability to work with existing devices that have only single physical sensor data and its potential robustness against spoofing attacks on individual sensors. The difficulty of decoupling and modifying different measurement components determines the attack difficulty. The authors propose three ways to apply virtual sensors for measurand authentication: byproduct verification, measurer verification, and environment verification.
Case Study: Camera Motion Side Channels for Facial Recognition
The paper includes a case paper that demonstrates the synthesis of virtual IMUs from camera motion side channels to collect postural hand tremor information, which can then be used for measurand authentication in facial recognition applications.
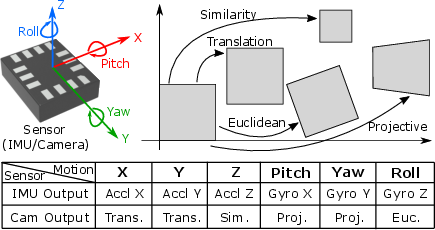
Figure 2: 2D image transformations corresponding to camera motion can be mapped to motion readings measured by physical IMUs.
The threat model involves spoofing attacks against smartphone facial recognition systems using silicone face masks. The synthesis methodology focuses on a model-informed approach that constructs virtual IMUs based on image registration concepts to extract both inter-frame and intra-frame motions.
Two methods are introduced: Image Transformation Estimation (ITE) for low-frequency information and Rolling Shutter Estimation (RSE) for high-frequency information. ITE measures the 2D image transformations needed to warp a reference frame to other frames, while RSE compares frames at the pixel level, leveraging the rolling shutter effect of CMOS cameras to capture high-frequency variations.
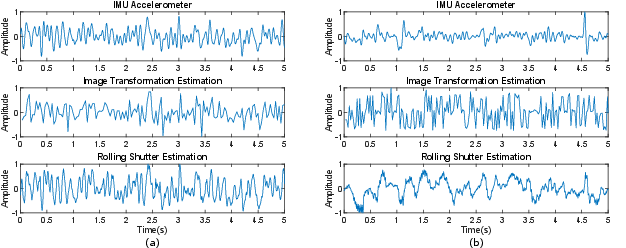
Figure 3: Measurements of physical IMU accelerometers and virtual IMUs synthesized with ITE and RSE methods show that disabling video stabilization enhances the capability of virtual sensors for measurand authentication.
Experiments conducted with four participants using a Google Pixel 2 smartphone showed that virtual IMUs using RSE achieved performance approaching that of physical IMUs in tremor recognition. The results indicated that integrating user postural hand tremor information from camera motion side channels could help defend against visual spoofing attacks, reducing false positive rates by up to 87.5%.
Discussion and Future Directions
The paper identifies several areas for future work, including the development of more concrete and computable mathematical models for sensor side channels, ensuring security during authentication by preventing eavesdropping and transduction attacks, and exploring the potential of sensor repurposing to reduce the number of physical sensors needed in various applications. The authors suggest that with active controls and dedicated APIs, sensor side channels could evolve into legitimate communication channels, necessitating periodic examination of their security implications.
Conclusion
This paper successfully argues that analog sensor side channels can provide defenders with valuable opportunities to authenticate sensor measurands. By actively controlling sensor side channels and synthesizing virtual sensors, it is possible to enhance the security and functionality of existing systems, paving the way for new research areas that integrate digital forensics, sensor fusion, and multimodal deep learning.
Follow-up Questions
- How does the proposed virtual sensor synthesis framework enhance multimodal authentication compared to traditional approaches?
- What are the implications of using analog sensor side channels in defending against spoofing attacks?
- How do the ITE and RSE methods differ in extracting low- and high-frequency sensor information?
- What challenges remain in integrating virtual sensors with existing authentication systems for improved security?
- Find recent papers about virtual sensor synthesis.
Related Papers
- Privacy Side Channels in Machine Learning Systems (2023)
- Side Eye: Characterizing the Limits of POV Acoustic Eavesdropping from Smartphone Cameras with Rolling Shutters and Movable Lenses (2023)
- Improving the Authentication with Built-in Camera Protocol Using Built-in Motion Sensors: A Deep Learning Solution (2021)
- Biometric Face Presentation Attack Detection with Multi-Channel Convolutional Neural Network (2019)
- Deep-Spying: Spying using Smartwatch and Deep Learning (2015)
- Opportunistic Sensor-Based Authentication Factors in and for the Internet of Things (2024)
- Sensor Security: Current Progress, Research Challenges, and Future Roadmap (2022)
- Attack Resilience and Recovery using Physical Challenge Response Authentication for Active Sensors Under Integrity Attacks (2016)
- Mobile Device Identification via Sensor Fingerprinting (2014)
- Glitch in Time: Exploiting Temporal Misalignment of IMU For Eavesdropping (2024)