- The paper presents two predictive models that forecast disruptive innovations, revealing a new DI approximately every 4.6 years.
- The quantitative model employs linear regression while the qualitative analysis evaluates attributes like AI-driven synthetic media to predict cyber threats.
- The study highlights the integration of proactive defense measures with established frameworks to mitigate evolving cyber cognitive attacks.
Towards Proactive Defense Against Cyber Cognitive Attacks
The paper "Towards Proactive Defense Against Cyber Cognitive Attacks" (2510.15801) introduces a novel methodology to predict the emergence of disruptive innovations (DIs) and their exploitation in cyber cognitive attacks. The aim is to develop proactive defense strategies by harnessing both quantitative and qualitative predictive models. This approach addresses existing gaps in the literature where the focus has primarily been on categorizing existing attack tactics rather than anticipating future innovations and attacks.
Cyber Cognitive Attacks and Disruptive Innovations
Cyber cognitive attacks exploit psychological biases to manipulate decision-making processes, primarily facilitated through disruptive innovations like AI-driven disinformation and synthetic media. These attacks leverage Tactics, Techniques, and Procedures (TTPs) of adversaries to execute operations with precision and at scale. The authors highlight the inadequacy of traditional defenses against these advanced threats and propose leveraging frameworks like MITRE ATT&CK and DISARM for structured defense strategy development.
Methodology
DI Dataset Collection and Preprocessing
The methodology involves identifying and collecting historical DI data relevant to cognitive attacks. The focus is on post-cyber era technologies that transformed communication and data collection methods. The selection criteria ensure technologies like social media and AI are included due to their potential to enable substantial shifts in attack capabilities.
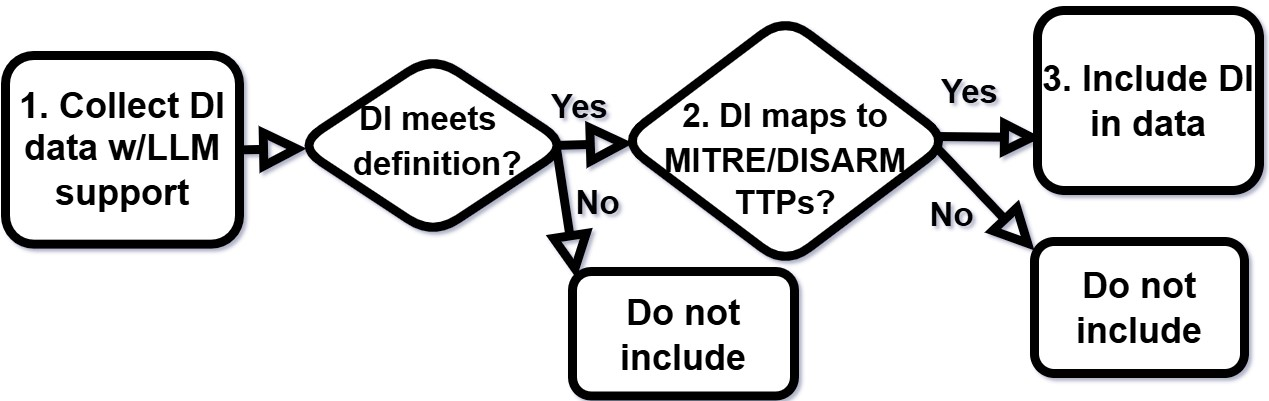
Figure 1: Procedure for preparing DI dataset.
Modeling and Prediction
The authors propose two predictive models:
- Model 1: Linear Regression - Predicts the year of future DI emergence based on past trends. The linear regression model revealed that significant new DIs appear approximately every 4.6 years, projected to occur around 2022.
- Model 2: Qualitative Analysis - Predicts the attributes of emerging DIs by scoring potential innovations across dimensions such as communication pathways and data collection. For example, AI synthetic media was identified with high impact in communication and social networking attributes.
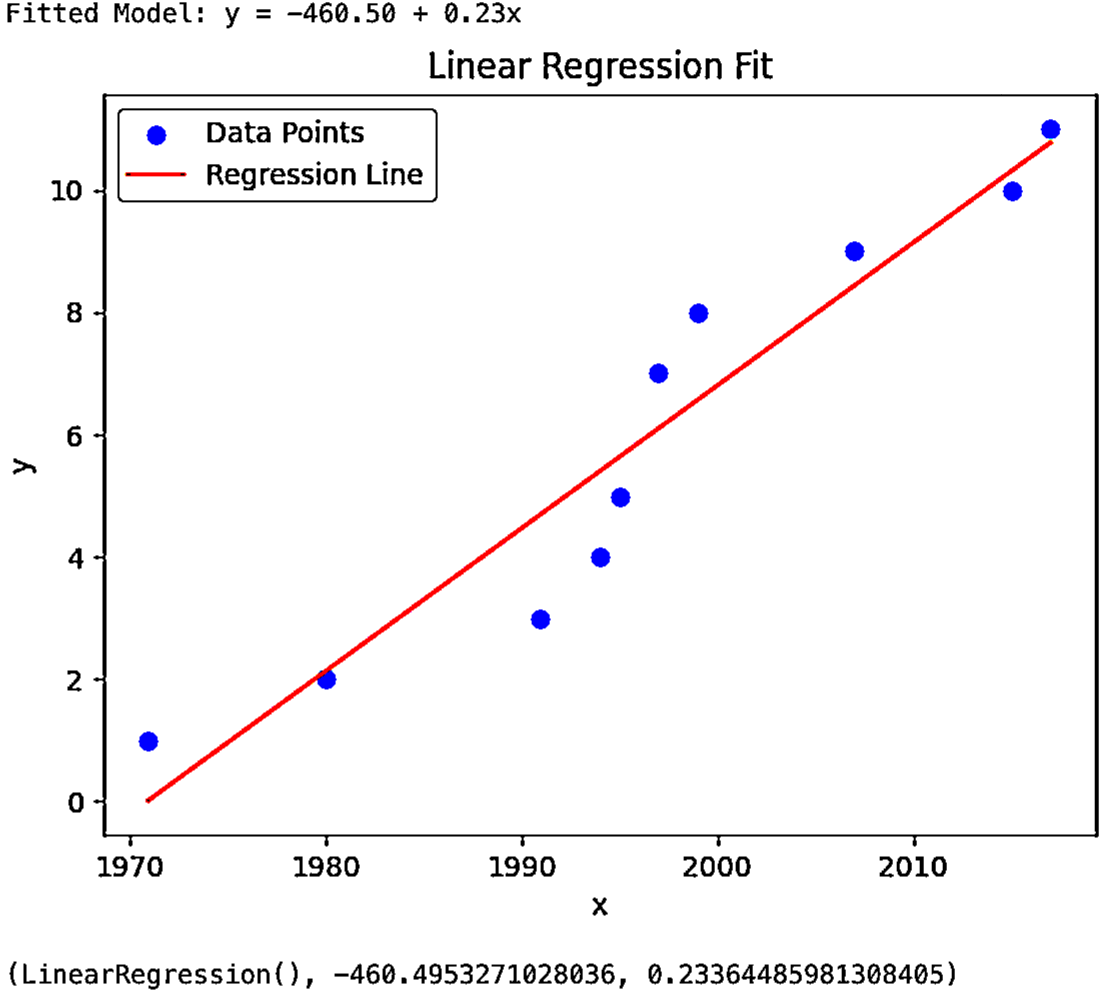
Figure 2: Linear regression of DI emergence timeline.
Case Study and Experimental Validation
A case paper analyzing 11 DIs between 1971-2017 demonstrated the predictive model's utility. The authors predict the emergence and potential malicious use of humanoid robots as a DI initially emerging in 2021. This inclusion is based on its profound implications for communication and data interactions, validated by trends in DI emergence timelines.

Figure 3: "Furhat" Robot experimentation at the US Air Force Academy (2023). Credit: Bonnie Rushing. The appearance of U.S. Department of Defense (DoD) visual information does not imply or constitute DoD endorsement.
Designing Proactive Defense
Leveraging the predicted attributes and timelines, the authors propose designing proactive defenses using predictive insights and existing defense frameworks:
- User Training - Mitigates spearphishing and manipulation threats by increasing awareness.
- Enterprise Policy - Restricts data access and enhances privacy controls for vulnerable technologies.
- Algorithm Modification - Adjust search and content presentation algorithms to minimize exploitation.
These strategies are designed to forestall potential threats posed by emerging DIs, allowing for timely and informed defense planning.
Conclusion
This paper presents a significant advancement in predicting and defending against cyber cognitive attacks by integrating prediction models with established defense frameworks. By forecasting DI emergence and defining their attributes, the research empowers stakeholders to develop proactive measures against potential cognitive attacks. Future work should extend these predictive models by incorporating larger datasets and embracing evolving technological paradigms. Cross-disciplinary collaboration will be crucial in mitigating the societal impacts of these cognitive advancements, ensuring resilience against adversarial tactics.


