- The paper introduces a proactive offensive security framework that uses threat simulation and red team exercises to reveal AI system vulnerabilities.
- Methodologies, including vulnerability assessments and penetration testing, are tailored to address AI’s stochastic and data-dependent risks.
- Integrating offensive security practices throughout the AI development lifecycle improves system robustness and guides effective remediation.
Offensive Security for AI Systems
AI systems are increasingly prevalent, necessitating robust security strategies that go beyond traditional defensive measures. This paper introduces a comprehensive framework for offensive security in AI, emphasizing proactive threat simulation and adversarial testing to identify and mitigate risks throughout the AI lifecycle. It examines key offensive security techniques tailored to address AI's unique susceptibilities and aims to bridge theoretical concepts with actionable methodologies for strengthening AI systems against emerging threats.
AI Development Lifecycle and Vulnerabilities
AI systems differ significantly from traditional IT systems due to their stochastic nature and data-driven behavior, which introduces unique vulnerabilities. The CRISP-ML(Q) model [studer2021crispmlq], an extension of CRISP-DM [wirth2000crisp], provides a structured framework for integrating quality assurance principles into machine learning workflows, facilitating the identification of security checkpoints throughout the AI development lifecycle. Foundational security measures are necessary but insufficient; proactive testing approaches are crucial for revealing latent vulnerabilities before deployment.
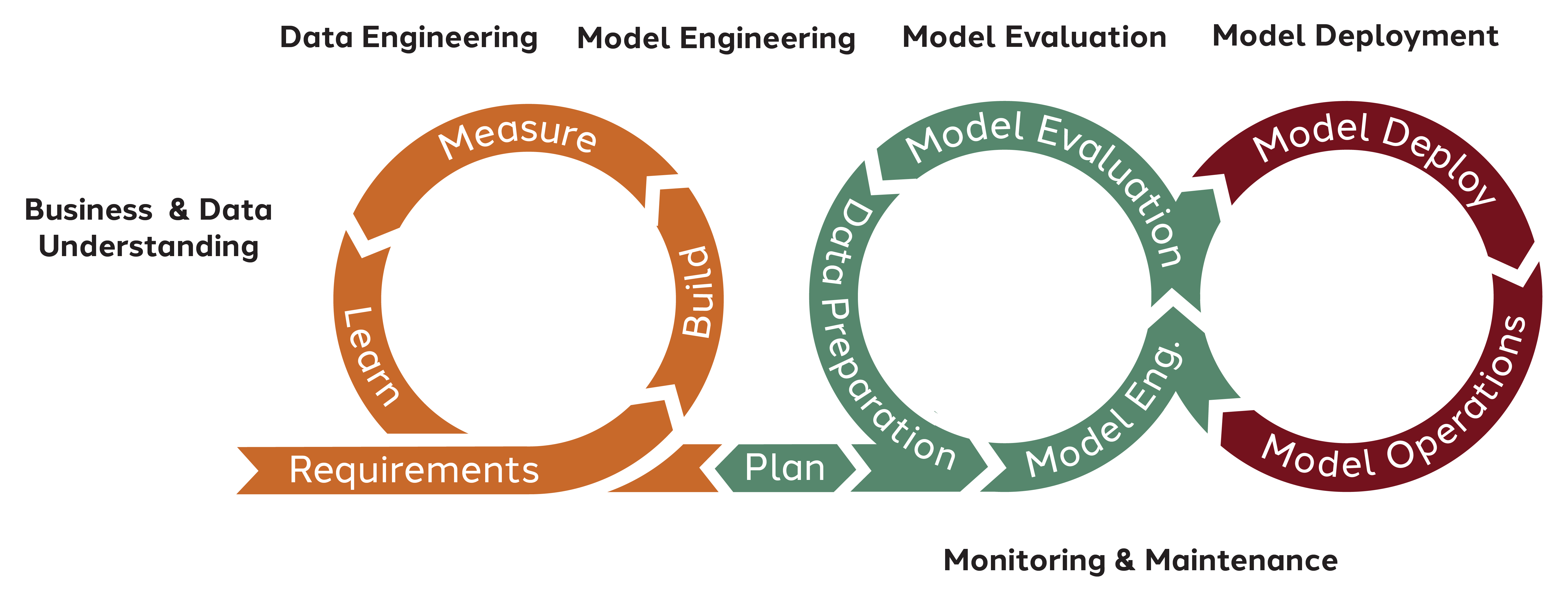
Figure 1: AI lifecycle based on CRISP-ML(Q) process model. This process highlights stages such as data engineering, model engineering, evaluation, deployment, and ongoing monitoring. Incorporating security and quality checks into each stage (data validation, model performance monitoring, etc.) is essential for AI system assurance.
AI models introduce security and privacy concerns not found in conventional software. They can memorize training data and unintentionally reveal sensitive information. Additionally, AI models often exhibit overconfidence, assigning high confidence scores to incorrect outputs, which can be exploited by attackers. Current AI security efforts emphasize defensive strategies, but structured offensive methods are gaining traction to uncover potential vulnerabilities [raney2024ai, harguess2023securing]. The AI Security Pyramid of Pain [ward2024pyramid] categorizes threats to prioritize protection efforts. Compromises at the data or model parameter level can undermine downstream defenses. The MITRE ATLAS and OWASP Top Ten lists map threat tactics to AI and machine learning systems, but comprehensive security frameworks for AI remain underdeveloped.
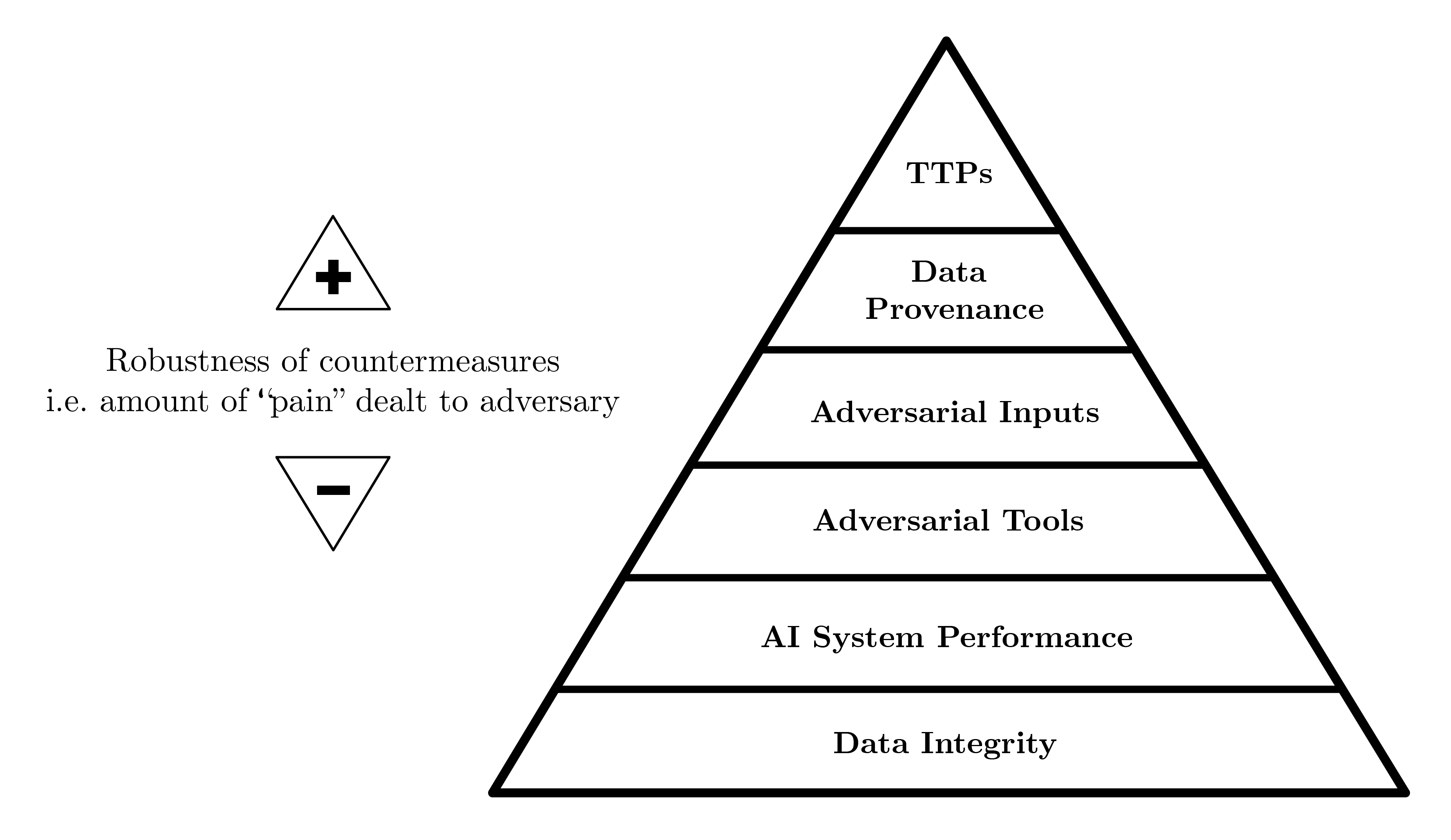
Figure 2: The AI Security Pyramid of Pain [ward2024pyramid].
Defensive vs. Offensive Security Paradigms
Defensive security (blue team) focuses on protecting AI systems, detecting intrusions, and responding to incidents, while offensive security (red team) adopts an adversarial mindset to identify vulnerabilities through simulated attacks. The Build–Attack–Defend triangle [miessler2016difference] connects development, offensive attacks, and defense, emphasizing information flow between teams for continuous improvement.
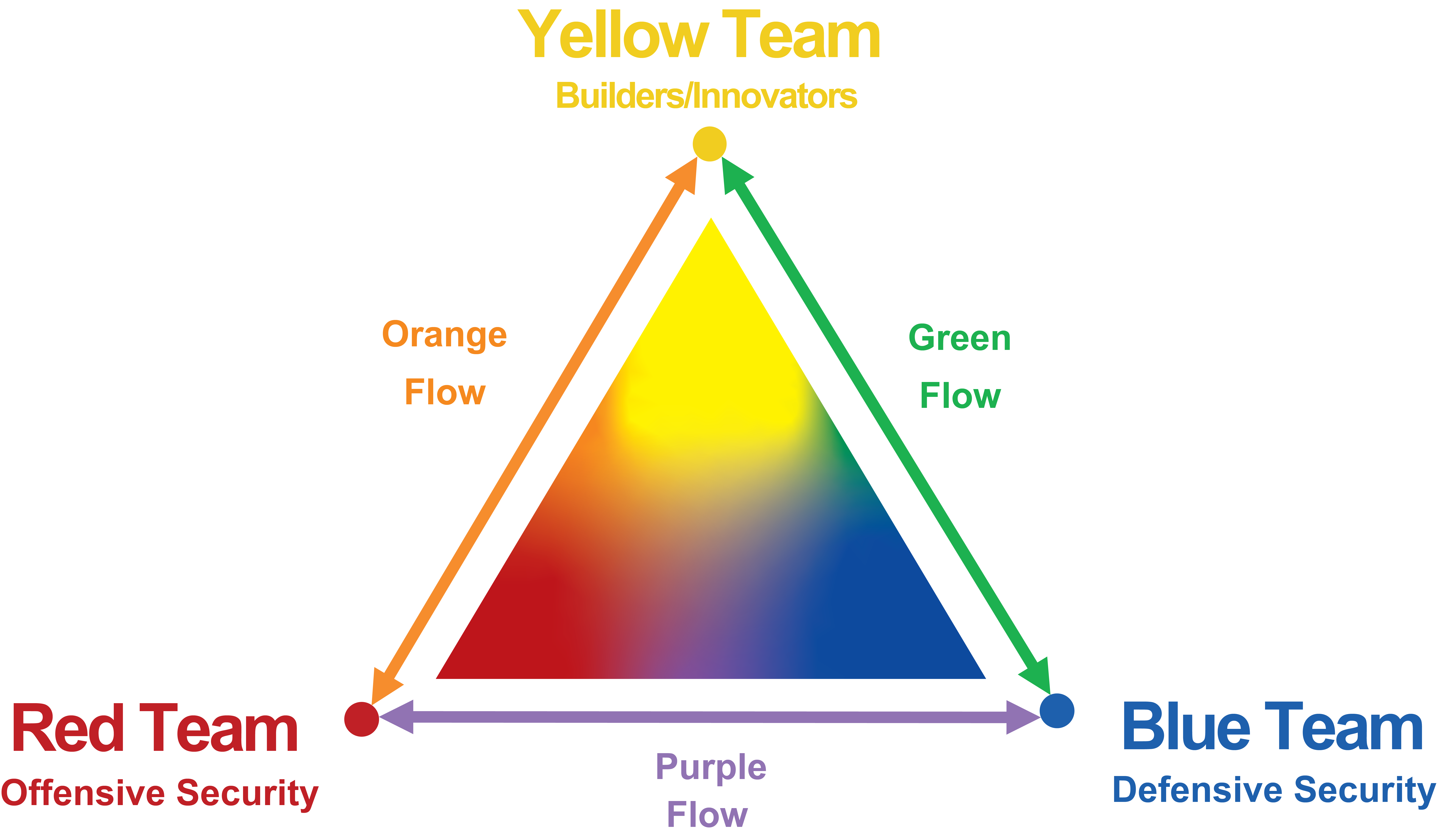
Figure 3: The Build–Attack–Defend triangle illustrates a secure ecosystem in which developers build the system (Yellow Team), defenders protect it (Blue Team), and attackers test it (Red Team). Information flows between teams include design inputs from developers to defenders, red team findings shared with defenders to improve monitoring, and offensive insights passed to developers to address design flaws. These exchanges support continuous security improvement across the AI lifecycle.
Blue teams implement security measures such as access controls, monitoring, and encryption, adapting them to AI's unique characteristics. Red teams, in contrast, use exploit development, fuzzing, and adversarial examples to uncover faults, demonstrating the real-world impact of weaknesses to guide remediation efforts. Effective security programs integrate both approaches, fostering collaboration between development, offensive, and defensive teams.
Offensive Security Methodologies
Offensive security for AI is organized into a hierarchy of increasing depth and adversarial realism, starting with vulnerability assessments, progressing to penetration testing, and culminating in red team engagements. Vest and Tubberville’s "Inverted Pyramid" model [vest2019redteam] describes this structure.
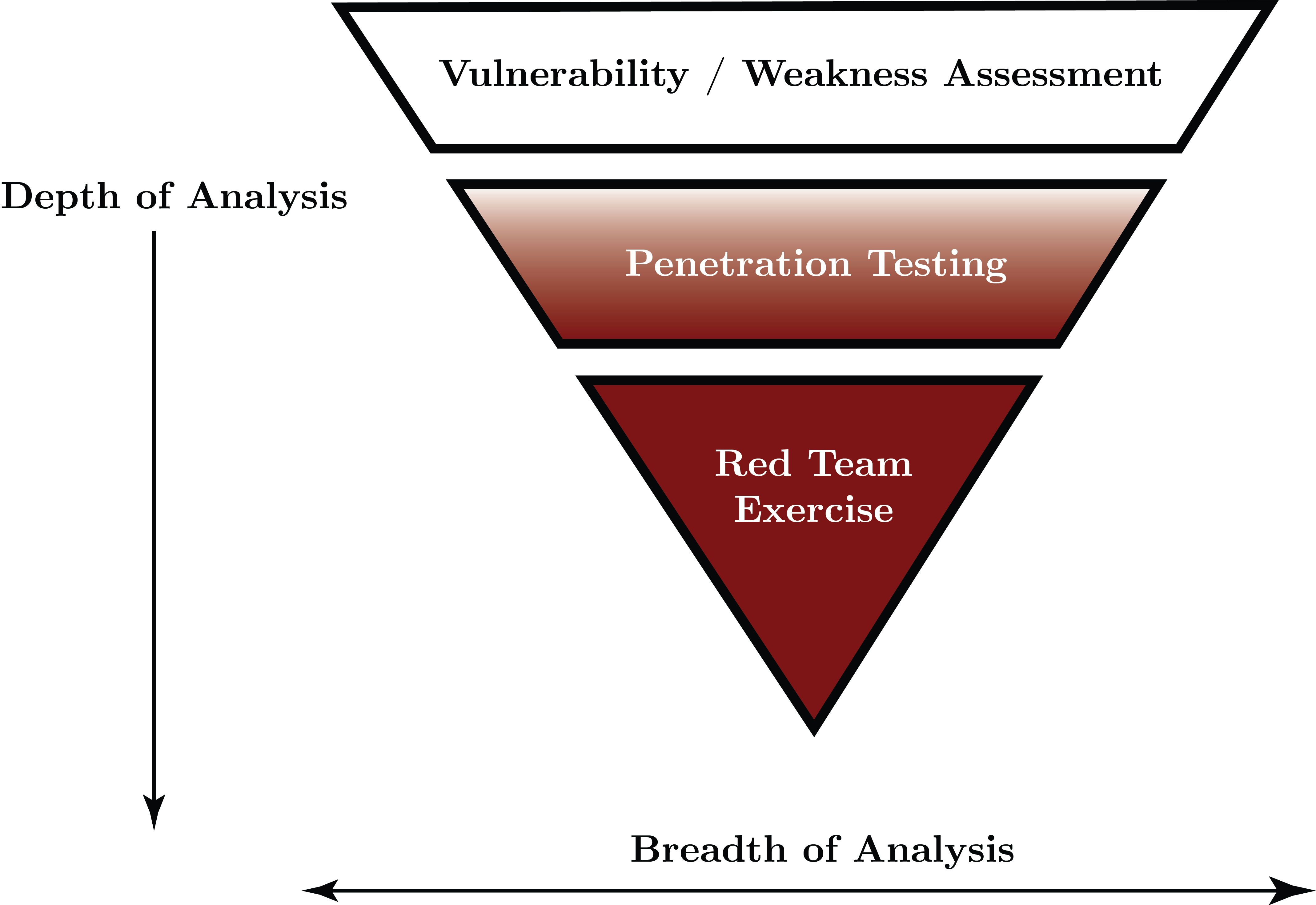
Figure 4: The Inverted Pyramid of Red Teaming.
Vulnerability assessments identify potential weaknesses without active exploitation, focusing on known issues in AI-specific components such as training data and model APIs. Penetration testing simulates attacks in a controlled environment, actively targeting and exploiting selected components to assess how vulnerabilities might be leveraged in practice. Red team engagements are comprehensive offensive security assessments in which a simulated adversary targets an AI system using realistic tactics to test the system's resilience under sustained, multi-vector attacks.
Conclusion
AI technologies reshape the security landscape, necessitating offensive security practices that account for AI-specific failure modes. Structured approaches like vulnerability assessments, penetration testing, and red team exercises allow practitioners to proactively identify and remediate weaknesses. Future directions include developing better tools for automating AI vulnerability discovery, creating evaluation metrics that reflect robustness under adversarial conditions, and enhancing knowledge sharing within the community. Harguess and Ward [harguess2023securing] emphasize post-engagement knowledge transfer as a formal part of the red teaming process.



