- The paper develops a resilient framework integrating a saturation-based observer, online attack detector, and distributed controller to mitigate compromised sensor measurements.
- It employs static and adaptive thresholds with redundant data exchange to accurately detect and isolate false sensor inputs, ensuring system reliability.
- Simulations confirm bounded error performance and finite-time convergence even with multiple compromised sensors, ensuring robust vehicle platoon formation.
Distributed Control under Compromised Measurements: Resilient Estimation, Attack Detection, and Vehicle Platooning
Introduction
The paper presents a robust framework for distributed control of networked vehicles under potentially compromised sensor inputs. This research addresses the challenges faced in maintaining accurate state estimates and stable vehicle formations in the presence of sensor attacks. The architecture integrates a resilient observer, an attack detector, and a distributed controller to ensure the system's resilience against deceptive signals.
Architecture Overview
The proposed architecture comprises three core components:
- Resilient Observer: The observer mitigates the impact of false data injection (FDI) by incorporating a saturation mechanism that limits the influence of potentially corrupted sensor measurements. The observer operates by dynamically adjusting the trust placed on sensor data, using a combination of static and adaptive thresholds.
- Attack Detector: An online distributed detection mechanism identifies and categorizes sensors into categories of being under attack, attack-free, or suspected. The detector cross-verifies data using redundant measurements from neighboring vehicles, ensuring that compromised sensors do not propagate errors through the system.
- Distributed Controller: Based on observer estimates, the controller achieves formation control by adjusting vehicle dynamics in real-time. It ensures that all vehicles maintain a predetermined formation, despite the presence of compromised sensor data.
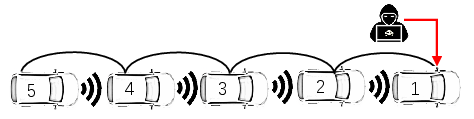
Figure 1: Platoon of five vehicles. The position and velocity measurements of vehicle 1 are compromised by a malicious attacker. Each vehicle is able to exchange messages with other vehicles nearby through wireless communication.
Implementation Details
Observer Design
The observer utilizes a saturation function applied to measurement innovations, effectively reducing the influence of any data anomalies. For vehicles within communication range L, the observer leverages redundant information to reconstruct potential true state estimates. The design includes:
- Static Threshold: A threshold βi is calculated based on a predefined worst-case scenario, ensuring stability within known attack limits.
- Adaptive Threshold: The system dynamically adapts to the attack severity by updating βi(t) to reflect changes in detection confidence over time.
The calculations for these thresholds are aligned with the constraints derived from vehicle and network capabilities, ensuring optimal resource use without compromising reliability.
Detector Operation
The detection process involves logical conditions assessing discrepancies in observed measurements versus expected behavior. By exchanging and processing data from nearby vehicles, the detector accurately identifies compromised nodes. The distributed nature ensures low latency in detection, crucial for maintaining operational integrity in dynamic environments.
Controller Functionality
The controller encompasses a feedback mechanism that stabilizes the vehicle platoon. It applies corrections based on discrepancies between estimated and desired states, using feedback from both absolute and relative positioning data.
The research shows, through simulations, that the proposed methods effectively maintain control robustness even when b sensors are compromised. Theoretical results demonstrate that for any noise level, the system achieves bounded errors. Furthermore, in a noise-free environment, the system can perfectly maintain the planned vehicle formation given the constraints and initial assumptions.
The architecture guarantees finite-time convergence of detection sets, ensuring timely updates to both estimation and control processes. Under defined system dynamics and control gains, the methodology assures asymptotic stability of the control system.
Conclusion
This integrated architecture presents a robust solution for distributed vehicle control systems subject to sensor attacks. By incorporating adaptive tools for estimation and detection, it allows for maintaining system stability and effectiveness even in adversarial settings. Future work may cover extended dynamic models and multi-dimensional vehicle network structures to further enhance the versatility and resilience of such systems.


