- The paper demonstrates that honey items in honeypots can effectively distinguish automated reconnaissance from manual, human-driven APT activities.
- The methodology deploys decoys such as fake credentials and invisible links, monitored via Elastic Stack to assess intrusion severity.
- The experiment underscores that deception techniques can reduce false positives compared to traditional methods, enhancing early APT detection.
Applying Deception Techniques for APT Detection
Introduction
The paper "Towards Identifying Human Actions, Intent, and Severity of APT Attacks Applying Deception Techniques -- An Experiment" (2006.01849) addresses the increasingly sophisticated threat of Advanced Persistent Threats (APTs) and explores the use of deception techniques as a method for their detection and analysis. APTs pose significant challenges for conventional signature-based and anomaly-based intrusion detection systems due to their stealthy nature and ability to exploit zero-day vulnerabilities. The authors propose deploying honey items within honeypots to distinguish between automated attacks and those requiring human interaction, thereby facilitating detection of APT activities.
Methodology
The experiment involves deploying various honey items within a Linux-based honeypot located in a private cloud environment. The honey items serve as decoys that are designed to trigger analysis when manipulated. These decoys include disallowed entries in the robot.txt file, invisible links in web pages, and fake credentials embedded within HTML comments. Furthermore, the researchers create a monitoring infrastructure centered around Elastic Stack, using a Kibana dashboard to oversee honeypot interactions and network activity.
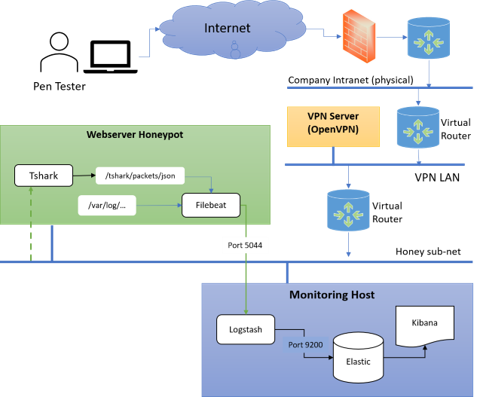
Figure 1: Experiment Set Up and Network Diagram.
The experiment simulates APT-type attacks by inviting penetration testers to mimic attackers with initial access inside the network perimeter. The interactions with honey items provide insight into the differentiation between automated and manual attacks, and the setup is designed to categorize attack severity based on engagement level with the decoy items.
Findings and Analysis
The findings delineate a clear distinction between automated and manual intrusions. Initial stages are characterized by automated reconnaissance using tools like Nmap, Nikto, and Burp Suite, as indicated by the detection of ICMP and TCP SYN packets. Subsequent manual interventions, such as attempts to use fake login credentials discovered in HTML comments, signify heightened intrusion intent.

Figure 2: Kibana Dashboard reflecting interactions with honey items and network activities.
High-priority indicators, such as the use and variation of fake credentials, demonstrate structured manual attacks. Penetration testers replicated APT behavior by first using automated scanning tools followed by more targeted actions requiring human reasoning. The experiment successfully showcases how honey items can identify attack severity and manually driven actions, distinguishing them from those executed solely by automated tools.
Figure 3 provides a schematic representation of the attack pattern highlighting the progression through various intrusion severity levels.

Figure 3: Attack State Diagram illustrating different intrusion severity levels based on detected user interactions.
Implications and Future Directions
The study illustrates the efficacy of deception techniques in identifying structured attacks within security perimeters, offering a potential tool for early identification of APT incidents. Distinguishing human-driven intrusions through honey items significantly reduces false positives compared to traditional intrusion detection methodologies. The paper opens pathways for further research into using deception techniques in production environments, potentially enhancing defenses against both insider and APT threats. Future work could explore more expansive deployment scenarios and integrate deception deeper within organizational infrastructure, facilitating a more comprehensive security posture.
Conclusion
This paper demonstrates the viability of deception techniques in discriminating between automated and human-driven cyber threats. The research paves the way for more effective detection strategies against APTs and insider threats within network environments. By exploiting the nuanced behavior elicited by carefully designed honey items, the approach provides an early detection mechanism while minimizing false positives inherent in traditional intrusion detection systems. Subsequent research can expand upon these findings by deploying deception techniques within larger, more diverse network configurations, potentially offering scalable solutions to combat sophisticated cyber threats.


