- The paper formalizes the threat model for MCP deployments, identifying vulnerabilities like content injection and supply chain attacks.
- It introduces comprehensive security controls including OAuth authentication, RBAC, provenance tracking, and sandboxing to mitigate identified risks.
- The paper integrates MCP security risks into existing governance frameworks while outlining new research directions for dynamic agent systems.
Securing the Model Context Protocol (MCP): Risks, Controls, and Governance
Introduction to MCP and Its Architecture
The Model Context Protocol (MCP) represents a significant advancement in integrating LLMs with external applications, enabling dynamic connections that replace traditional developer-controlled APIs. This standardization allows for efficient reuse of integrations across different platforms, facilitating enhanced context acquisition and operational execution. MCP comprises host, client, and server components, where the host acts as the user interface that interprets requests through an LLM, the client manages tool calls, and the server executes operations through tools and data resources. This architecture promotes seamless communication between AI applications and external systems.
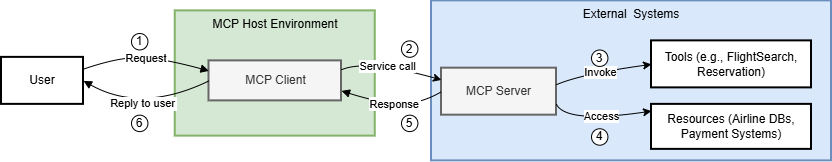
Figure 1: MCP Client-Server Architecture.
Adoption of MCP by leading AI companies has transformed traditional passive text generation into active task execution, significantly reducing time spent on routine tasks. However, as organizations embrace MCP, inconsistent security practices pose challenges that existing governance frameworks do not address.
Security Challenges in Dynamic Systems
Paradigm Shift
MCP introduces a shift from static systems, where security is governed by deterministic code analysis, to dynamic systems where agent behavior is determined by real-time data interaction. This adaptability is inherent to MCP, as agents must react to external stimuli for effective task execution. However, this dynamic nature enlarges the attack surface, exposing vulnerabilities such as content injection, where malicious instructions embedded in user-generated data are inadvertently executed by MCP agents.
Security Vulnerabilities
Real-world incidents exemplify the security flaws in MCP implementations. Examples include data exposure through bugs and prompt injection attacks in major enterprises, highlighting the urgency for refined authentication and access control mechanisms. Traditional security measures, such as input validation, are insufficient as agents interpret data continuously and dynamically, necessitating advanced security approaches.
MCP as a Risk Amplifier
MCP's flexibility amplifies risks through broadened access to data sources. Unauthorized data exfiltration can occur via malicious instructions when agents have access to interconnected systems. The "lethal trifecta" risk model, consisting of private data access, exposure to untrusted content, and external communication capabilities, highlights potential vulnerabilities.
Limitations of Existing Frameworks
Current AI governance frameworks primarily address model-level risks, such as fairness and transparency. They lack the infrastructure to manage the unique risks posed by MCP's dynamic and cross-system interactions. Consequently, organizations require new governance frameworks specifically tailored to the security challenges of MCP-enabled systems.
Contributions
This paper formalizes the threat model for MCP deployments, proposes comprehensive security controls, aligns these controls with existing governance frameworks, and establishes a broader research agenda for securing dynamic agent systems. The contributions are structured around threat identification, control framework development, governance integration, and exploration of future research directions.
Threats and Attack Vectors
Developer-User Boundary Blurring
MCP's democratization of integration allows end-users to establish connections between systems without deep technical knowledge. This can inadvertently introduce security vulnerabilities, as users may grant broad access to sensitive data without understanding the implications.
Three Adversary Types
Security challenges derive from content injection adversaries, supply chain adversaries, and inadvertent agent adversaries, each exploiting different weaknesses within the MCP ecosystem. Understanding these adversaries is crucial for effective defense strategies.
Attack Mechanisms
Data-driven attacks exploit the dynamic data processing capabilities of agents, leading to potential data exfiltration threats. Supply chain attacks arise from untrusted MCP server installations, with risks compounded by the ease of connecting multiple servers.
Configuration and Governance Risks
Even trusted MCP servers pose configuration challenges, such as over-permissioning and inconsistent authentication practices, necessitating refined, role-based access control strategies to safeguard sensitive operations.
Security Controls and Defense Framework
The defense strategy comprises five categories: authentication/authorization, provenance tracking, sandboxing, policy enforcement, and centralized governance.
Authentication and Authorization
Implementing per-user OAuth authentication and role-based access control (RBAC) mitigates governance gaps, while ensuring user-level audit capabilities.
Provenance Tracking
Comprehensive logging provides visibility into all agent actions, fostering reproducibility, compliance, and forensic capabilities.
Context Isolation and Sandboxing
Mandatory containerization of MCP servers ensures environment isolation, preventing arbitrary code execution and enabling input/output filtration.
Policy Enforcement
Inline data loss prevention (DLP) and secrets scanning maintain the integrity of data interactions, while role-specific enforcement prevents unauthorized agent actions.
Centralized Security Governance
Centralized governance incorporates private registries, tool access policies, sandbox infrastructure, and server execution standards to maintain consistent security practice across the organization.
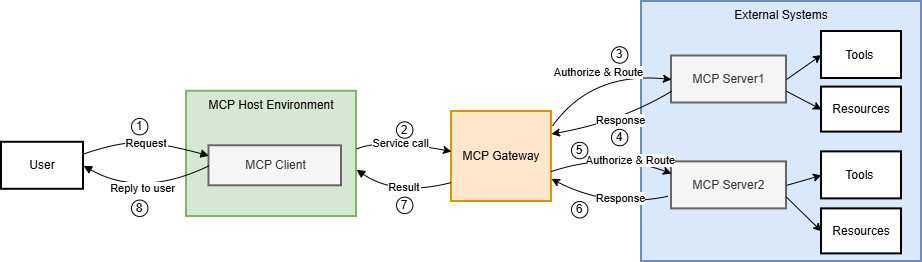
Figure 2: MCP Gateway Architecture.
The gateway architecture consolidates security controls, facilitating a unified enforcement point that shifts security responsibilities from users to centralized administrators.
Governance and Implementation
Aligning MCP security practices within established frameworks enhances regulatory compliance. This mapping ensures that MCP security integrates seamlessly into existing compliance programs.
Open Research Problems and Conclusion
The dynamic nature of MCP presents new research opportunities in areas such as dynamic agent behavior analysis, verifiable registries, formal verification, privacy-preserving operations, and automated security policy generation.
The MCP framework fundamentally alters AI system integration. Addressing security challenges proactively ensures that MCP realizes its potential while safeguarding data integrity and privacy. This research lays the foundation for robust security modeling in dynamic environments through comprehensive threat mitigation strategies.



