- The paper introduces HoneyBadger, which uses symbolic execution and heuristics to efficiently detect honeypot scams in Ethereum smart contracts.
- It establishes a detailed taxonomy categorizing honeypots into EVM, Solidity, and Etherscan levels based on specific vulnerabilities.
- Evaluation shows HoneyBadger achieved an 87% true positive rate, analyzing over 150,000 contracts and identifying 460 unique honeypots.
The Art of The Scam: Demystifying Honeypots in Ethereum Smart Contracts
This essay provides an analytical overview of the concepts and findings presented in the paper titled "The Art of The Scam: Demystifying Honeypots in Ethereum Smart Contracts". The study presents a systematic examination and taxonomy of Ethereum smart contract-based honeypots, implementing a detection tool named HoneyBadger, and elucidating their prevalence and economic implications within the Ethereum ecosystem.
Introduction
The paper addresses a novel trend in Ethereum smart contracts, known as "honeypots". Unlike traditional Ponzi schemes, where attackers look for existing vulnerabilities, honeypots are smart contracts that intentionally present a deceptive programming flaw to lure unwitting users into committing funds. Instead of relying on finding and exploiting vulnerabilities in others' contracts, attackers deploy honeypots to seek victims actively. Ethereum's ascent in value has fostered a fertile environment for such scams, motivating extensive investigations into these smart contracts' anatomy and implications.
Taxonomy of Honeypots
Honeypots on the Ethereum blockchain are demystified through an innovative taxonomy, classifying them into three categories:
- Ethereum Virtual Machine (EVM) Level:
- Solidity Compiler: Exploits vulnerabilities originating from the Solidity compiler.
- Inheritance Disorder: Appears in cases where variables are re-declared, as shown in (Figure 1).
- Skip Empty String Literal: Takes advantage of how the Solidity encoder handles empty strings leading to misalignment of function arguments.
- Type Deduction Overflow: Relies on integer overflow due to improper
var type deduction (Figure 1).
- Uninitialised Struct: Utilizes uninitiated variables to deceive unaware users, similar to the example seen in (Figure 1).
- Etherscan Blockchain Explorer: Uses the limitations of the Etherscan interface to mislead users.
- Hidden State Update: Conceals state-altering functions without visible transaction evidence on Etherscan, diverting funds to honeypot creators, exemplified in (Figure 1).
- Hidden Transfer: Exploits Etherscan's interface design to hide transaction details via lengthy code lines (Figure 2).
- Straw Man Contract: Utilizes a seemingly innocuous but replaced smart contract for funds misdirection, as presented in (Figure 1).
The taxonomy cataloged a diverse set of techniques, emphasizing the varied and sophisticated methods employed by attackers.
HoneyBadger
Design and Implementation
HoneyBadger is introduced as a specialized tool capable of analyzing EVM bytecode to detect honeypots using symbolic execution and well-defined heuristics aligned with the identified taxonomy (Figure 3). It's designed to efficiently handle the bytecode for over 2 million smart contracts present on Ethereum, considering their significant duplication rate. HoneyBadger's architecture comprises three primary components: symbolic analysis, cash flow analysis, and honeypot analysis. The engine modifies pre-existing symbolic execution methods to identify honeypot strategies effectively. Symbolic execution facilitates the exploration of all possible program paths, essential for discerning complex honeypot tactics that might lead to fraudulent traps.
Evaluation
The evaluation of HoneyBadger involved a large-scale analysis of 151,935 unique smart contracts. The tool demonstrated a high degree of efficiency, flagging approximately 460 unique honeypots within an average analysis time of 142 seconds per contract. The detection results highlighted 690 identified honeypots, including balance disorders, inheritance disorders, and hidden state updates as prominent techniques. HoneyBadger's validation process delivered an 87% overall true positive rate, underscoring its accuracy and efficacy in detecting honeypots with minimal false positives (Figure 4 & Figure 5).

Figure 4: Number of detected honeypots per technique.
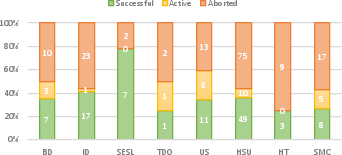
Figure 5: Number of successful, active and aborted honeypots per honeypot technique.
Insights and Implications
The analysis centered on discerning the effectiveness, behavior, diversity, and profitability of identified honeypots, revealing insights into the nature and operations of these frauds. The study observed that honeypots are often successful shortly after being deployed (often within 24 hours), suggesting victims promptly attempt to exploit perceived vulnerabilities. Most honeypots manage to attract a single victim, and comments left by users on Etherscan serve as a notification system that can lead to the cessation of fraudulent contracts. Despite this, numerous honeypots continued to succeed even post-commentary, indicating either a lack of due diligence by subsequent victims or the exploits' inherent allure (Figure 6 & Figure 7).

Figure 8: Number of monthly deployed honeypots per honeypot technique.

Figure 7: A word cloud generated from the comments on Etherscan.
Future Directions
The authors discuss the limitations such as the difficulty in bytecode-level detection of certain techniques due to lack of source code access and the inherent complexity of smart contract bytecode. Future research may focus on advancing detection methodologies by integrating machine learning to enhance the scalability and adaptability of honeypot detection frameworks. Additionally, there is potential in broadening the investigatory scope to uncover auxiliary scams connected to honeypots, thus deepening the understanding of these fraudulent activities' network. Tools like HoneyBadger are imperative for curbing financial losses incurred by victims in the Ethereum ecosystem, emphasizing the need for ongoing vigilance and development of detection solutions.
Conclusion
This paper presents a thorough examination of Ethereum-based honeypots, elucidating their functioning, prevalence, and economic impact. Through an innovative taxonomy, the research categorizes various honeypot techniques, which serve as a framework to guide future detection research and user education. The development and deployment of HoneyBadger revealed a sizeable presence of honeypots on the blockchain and their potential for financial exploitation. The findings underscore the necessity for continuous advancements in detection methodologies, potentially integrating machine learning to counter evolving threats in the blockchain landscape.




