- The paper demonstrates that a data-driven ML approach to load shedding can mitigate instability attacks with 92% accuracy on the IEEE 14 Bus System.
- It integrates a time-series encoder and a load index encoder with a three-layer MLP classifier for adaptive, context-sensitive decision-making.
- The study reveals that static, topology-based schemes can worsen grid instability, underscoring the need for dynamic, real-time mitigation measures.
Machine-Learning Driven Load Shedding for Instability Attack Mitigation in Power Grids
Introduction
This paper addresses the challenge of defending power grids against instability attacks—a class of cyber-physical attacks that introduce destabilizing feedback into the grid, potentially leading to catastrophic system-wide failures. Traditional load shedding schemes, which are typically topology-driven and pre-determined, are shown to be inadequate in the face of such attacks. The authors propose a data-driven, supervised ML approach to retrofit existing load shedding mechanisms, enabling adaptive, context-sensitive responses to instability attacks. The methodology is validated on the IEEE 14 Bus System using the Achilles Heel Technologies (AHT) Power Grid Analyzer, with a focus on both attack detection and optimal load shedding decision-making.
Instability Attacks and the Need for Data-Driven Load Shedding
Instability attacks differ fundamentally from conventional grid threats by exploiting feedback mechanisms to induce small-signal instability, often through hard-to-detect entry points. The paper demonstrates that naive application of traditional under-voltage load shedding can exacerbate instability under attack conditions, as illustrated by the divergent outcomes when shedding the same load under different attack scenarios.


Figure 1: (a) Naive load shedding under instability attack worsens system voltage; (b) alternative attack with same shed load restores stability, highlighting the non-triviality of optimal load selection.
This observation motivates the need for a data-driven approach, as the mapping from load shed action to system stability is highly context-dependent and not solely determined by network topology.
System Modeling and Data Generation
The IEEE 14 Bus System serves as the testbed, modeled in the AHT Power Grid Analyzer. The system comprises generators (red circles) and buses (white nodes), each with associated loads.

Figure 2: The IEEE 14 Bus System as modeled in the AHT Power Grid Analyzer, with generators and load buses.
To generate training data, the authors simulate a comprehensive set of attack and load shedding scenarios. For each configuration, system states are recorded before and after load shedding, and outcomes are labeled as "stable" or "unstable" using a heuristic based on absolute excursions, variance, and envelope slope of key signals. Modified Prony Analysis (MPA) is also implemented as a robust, data-driven method for early detection of unstable modes, serving as an alarm to trigger the ML-based defense mechanism.
Model Architecture and Training
The core of the proposed solution is a classifier that predicts, given the current system state and a candidate load to shed, whether the action will stabilize or destabilize the grid. The architecture consists of:
- Time-Series Encoder: Processes C×T input (channels × time) using two layers of 1D convolution, max pooling, and a Bi-GRU to extract temporal features.
- Load Index Encoder: Encodes the load index via a single-layer MLP.
- Classifier Head: Concatenates the encoded features and passes them through a three-layer MLP (128, 64, 2 units) with softmax output for binary classification.
The model contains approximately 600,000 parameters and is lightweight enough to be trained on commodity hardware.
Empirical Results
The classifier achieves an overall accuracy of 92% on the test set, with a stable-shed precision of 95% and recall of 68% at a conservative confidence threshold (τ=0.03). This thresholding strategy prioritizes minimizing false positives for stable actions, which is critical in safety-critical infrastructure.
Analysis of the data reveals that no single load is universally optimal for shedding across all attack scenarios, underscoring the inadequacy of static, topology-based schemes.
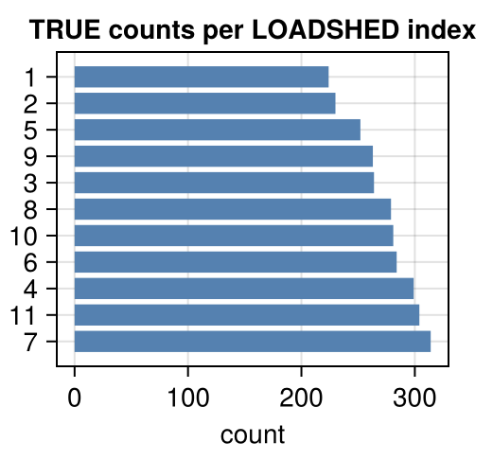
Figure 4: Distribution of stable sheds per load across all attack configurations; no load is consistently optimal, supporting the need for data-driven selection.
Further, the dataset encompasses a broad range of attack read/write variable combinations, ensuring that the model is exposed to diverse scenarios.
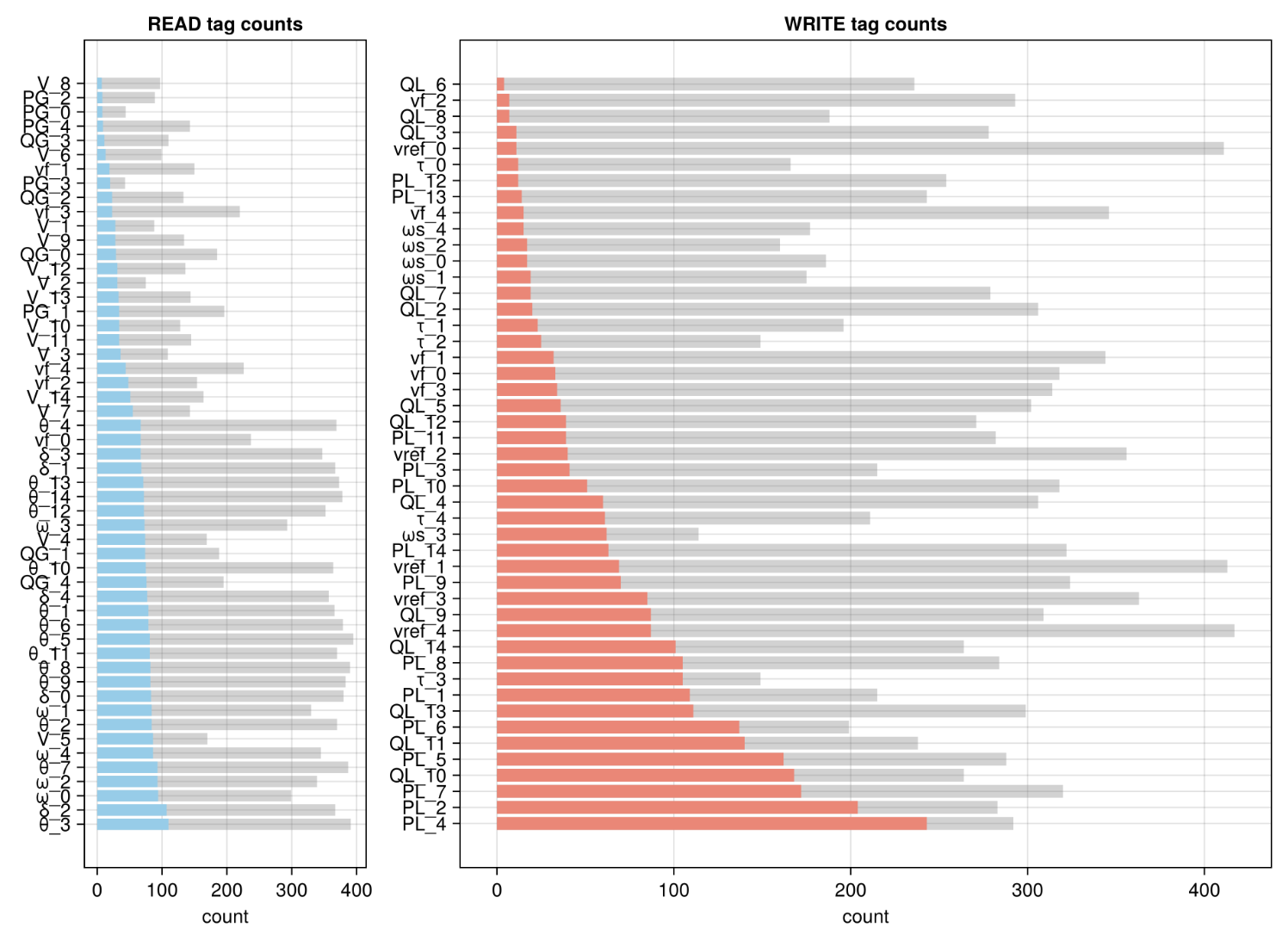
Figure 3: Distribution of stable shed cases across variable categories, demonstrating coverage of the attack configuration space in the training data.
Discussion
Strengths
- Context-Aware Decision-Making: The ML model enables adaptive selection of viable load sheds, outperforming static schemes that can inadvertently worsen instability.
- Integration with Existing Infrastructure: The approach leverages existing measurement and control infrastructure, requiring only software-level retrofitting.
- Scalability and Efficiency: The model is computationally lightweight and can be trained and deployed on standard hardware.
Limitations
- Data Availability and Latency: The approach assumes high-resolution, system-wide state measurements, which may not be available in legacy SCADA environments. Latency in data collection and actuation could limit real-time applicability.
- Data Integrity: The model's effectiveness is contingent on the integrity of sensor data. Sensor spoofing or data corruption could undermine defense efficacy.
- Decentralization Challenges: While the current model assumes centralized decision-making, decentralized deployment raises concerns about coordination and the risk of cascading failures from simultaneous, uncoordinated actions.
Implications and Future Directions
The work demonstrates that ML-driven load shedding can provide a practical, cost-effective defense against instability attacks, with the potential for integration into real-world grid operations. Future research directions include:
- Robustness to Adversarial Inputs: Incorporating adversarial training to enhance resilience against sensor spoofing.
- Decentralized and Multi-Agent Extensions: Developing coordination protocols for distributed deployment.
- Extension to Larger, Realistic Grids: Scaling the approach to more complex, heterogeneous power systems.
- Online Learning and Adaptation: Enabling continual learning to adapt to evolving attack strategies and grid configurations.
Conclusion
This paper establishes a data-driven, ML-based framework for adaptive load shedding in response to instability attacks on power grids. By demonstrating the inadequacy of traditional schemes and providing a practical, software-based solution, the work lays the foundation for robust, scalable defenses against emerging cyber-physical threats. The approach's strengths in adaptability and integration are balanced by challenges in data infrastructure and robustness, which present fertile ground for future research and development.






