- The paper presents EF/CF, which leverages transpilation of EVM bytecode to native C++ to achieve high-throughput fuzzing and precise exploit generation.
- It models complex interactions such as reentrancy and cross-contract calls, overcoming scalability limits and reducing false alarms in smart contract analysis.
- EF/CF achieves over 24,000 test cases per second and detects 99.9% of access control bugs, including compositional reentrancy attacks in multi-contract setups.
Introduction and Motivation
The paper presents EF/CF, a high-throughput fuzzing framework for Ethereum smart contracts, designed to address the increasing complexity and interdependencies of modern contracts. Existing analysis tools, including symbolic execution, model checking, and static analysis, suffer from scalability limitations and high false alarm rates when applied to contemporary smart contracts. EF/CF introduces a novel approach by transpiling EVM bytecode to native C++ code, enabling the reuse of optimized fuzzing toolchains and significantly increasing fuzzing throughput. The framework also models complex contract interactions, such as reentrancy and cross-contract calls, with high fidelity, allowing for the automatic generation of exploit transaction sequences.
















Figure 1: The complexity of Ethereum smart contracts, measured by lines of code, public functions, comparison operators, and branches, has increased steadily over time.
Problem Statement: Complexity and Interactions
Smart contract analysis is challenged by the stateful nature of contracts and the exponential growth in the space of possible transaction sequences. The paper demonstrates that contract complexity has increased in all measured aspects, with recent contracts averaging over 500 lines of code and 16 state-changing public functions. This complexity necessitates longer and more intricate transaction sequences to reach exploitable states, which most existing tools cannot handle efficiently. Furthermore, the frequent interaction between contracts, especially in DeFi applications, introduces compositional security issues and sophisticated reentrancy attack vectors that are not accurately modeled by prior tools.

Figure 2: Example of a contract with bypassable reentrancy-locking, illustrating an attack requiring two colluding attacker-controlled contracts.
EF/CF Architecture and Design
EF/CF is architected around two core principles: maximizing test case throughput and accurately modeling adversarial interactions. The system operates in two phases:
EF/CF's input format supports fuzzing the blockchain environment, transaction return data, reentrant transactions, and multi-contract targeting. The transaction sequence is modeled as a tree, allowing exploration of various reentrancy patterns, including cross-function and cross-contract reentrancy. The system enforces practical limits on call depth and reentrancy to avoid state explosion.

Figure 4: Mutation of transaction sequences to generate reentrant transaction trees with different shapes, enabling exploration of complex attack vectors.
Compositional Security and Multi-Contract Analysis
EF/CF supports compositional analysis by allowing the fuzzer to target multiple contracts and import custom blockchain states. This enables the detection of vulnerabilities that only manifest when contracts are composed, such as the Uniswap/IMBTC reentrancy exploit. The framework can synthesize Solidity attack contracts from generated test cases, facilitating end-to-end exploit reproduction.


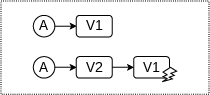

Figure 5: Illustration of single-contract and multi-contract transaction sequences, highlighting the difference between reentrancy and compositional attacks.
Implementation Details
The evm2cpp compiler performs basic block-level translation of EVM bytecode to C++, leveraging constant propagation and local data-flow analysis to optimize stack operations and eliminate interpreter overhead. The generated C++ code is instrumented for coverage and paired with a lightweight, fuzzing-optimized EVM runtime. The custom mutator, ethmutator, performs structure-aware mutations on transaction sequences and ABI-encoded inputs, using a dictionary seeded with constants extracted from the bytecode.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
pc_5a : {
// JUMPDEST
// CALLVALUE
const uint256_t v_1_0 = callvalue_v();
// DUP1
// ISZERO
const uint256_t v_3_0 = iszero_v(v_1_0);
// PUSH2 0x66
// JUMPI
if (v_3_0) {
ctxt->s.push(v_1_0);
goto pc_66;
}
ctxt->s.push(v_1_0);
goto pc_62;
} |
Example of basic block translation, showing elimination of redundant stack operations and direct control flow.
Evaluation
Scalability
EF/CF is the only tool in the benchmark capable of analyzing contracts requiring long transaction sequences (up to 10+ transactions) and complex state setups. Symbolic execution tools perform well on input constraints but struggle with path explosion in contracts with loops or arrays. Classic fuzzers fail to generate long transaction sequences, while hybrid tools inherit the slow input generation of symbolic execution.






























































Figure 6: Scalability results showing analysis time as a function of required transaction sequence length across multiple tools.
Throughput and Coverage
EF/CF achieves test case execution rates exceeding 24,000 per second, an order of magnitude higher than other fuzzers (Echidna: ~189/sec, Confuzzius: ~78/sec). The combination of native code execution and structure-aware mutations results in superior code coverage, especially on complex contracts.
Bug Detection
EF/CF detects 99.9% of access control bugs identified by EthBMC and finds additional vulnerabilities in contracts EthBMC could not analyze. For reentrancy, EF/CF accurately detects only exploitable bugs, avoiding the high false alarm rates of heuristic-based tools. In the Sailfish dataset, only 5 out of 26 reported reentrancy bugs are actually exploitable for Ether theft, as confirmed by EF/CF.
Compositional Attacks
EF/CF is the first dynamic analysis tool to generate exploits for compositional reentrancy attacks, such as the Uniswap/IMBTC case, synthesizing transaction sequences that reproduce the attack in a live blockchain environment.
Implementation Trade-offs and Limitations
- Ahead-of-time compilation sacrifices interpreter flexibility but enables aggressive optimization and high throughput.
- No support for dynamic contract creation; contracts that create new bytecode at runtime are not fuzzed.
- Bug oracle focus on Ether gains minimizes false alarms but may miss token-specific or liveness bugs.
- Custom mutator and dictionary-based input generation are essential for solving input constraints and generating valid transaction sequences.
Implications and Future Directions
EF/CF demonstrates that high-throughput, coverage-guided fuzzing, combined with accurate modeling of adversarial interactions, can scale to the complexity of modern smart contracts and generate concrete exploits. The approach bridges the gap between symbolic execution and fuzzing, offering comparable constraint-solving capabilities while avoiding path explosion. The open-source release of EF/CF and its benchmarks provides a foundation for further research in smart contract security, including multi-contract analysis, compositional security, and the development of more expressive bug oracles.
Conclusion
EF/CF advances the state-of-the-art in smart contract analysis by combining native code execution, structure-aware mutation, and precise modeling of complex interactions. The framework achieves superior scalability, throughput, and accuracy in bug detection, particularly for reentrancy and compositional vulnerabilities. Its design and implementation offer practical solutions for automated exploit generation and comprehensive security testing of Ethereum smart contracts, with significant implications for the security of DeFi and blockchain applications.










