- The paper introduces FaaSGuard, a complete DevSecOps framework that embeds security measures in every stage of the CI/CD pipeline for serverless applications.
- It validates the approach on OpenFaaS using real-world functions, achieving 95% precision and 91% recall in detecting vulnerabilities such as insecure dependencies and misconfigurations.
- The implementation effectively mitigates injection attacks, resource exhaustion, and supply chain threats while maintaining operational efficiency with minimal latency impact.
Secure CI/CD for Serverless Applications with FaaSGuard: An OpenFaaS Case Study
The paper "FaaSGuard: Secure CI/CD for Serverless Applications -- An OpenFaaS Case Study" focuses on the challenges and solutions associated with implementing a full lifecycle DevSecOps pipeline tailored for serverless computing environments, particularly in open-source platforms such as OpenFaaS.
Introduction to Serverless Security Challenges
Serverless computing abstracts infrastructure management, enabling modular and event-driven deployments. While this offers scalability and quick deployments, it presents significant security challenges. These include over-privileged functions, dependency vulnerabilities, and injection attacks that occur more frequently in open-source environments where developers need to secure the stack without cloud provider-managed tooling. Serverless applications, characterized by ephemeral and stateless functions, disrupt established DevOps practices for CI/CD orchestration, requiring integrated security strategies.
FaaSGuard Design and Implementation
Pipeline Framework
FaaSGuard integrates security into every phase of the development lifecycle—Plan, Code, Build, Deploy, and Monitor—by embedding lightweight, fail-closed security checks. It addresses threats such as injection attacks and resource exhaustion using empirically validated methods.
Development Phase:
- Plan: Predicated on threat modeling to verify architectural changes before code integration.
- Code: Utilizes static analysis to prevent insecure code from propagating to runtime. Code commits that elevate security risks are systematically blocked at compile time.
Operation Phase:
- Build: Focuses on preventing supply chain attacks by securing dependencies and image configurations.
- Deploy: Treats each release as an audited transaction, ensuring signed integrity and policy compliance.
- Monitor: Deploys anomaly detection and adaptive rate limiting to counteract runtime threats such as "denial-of-wallet" scenarios.
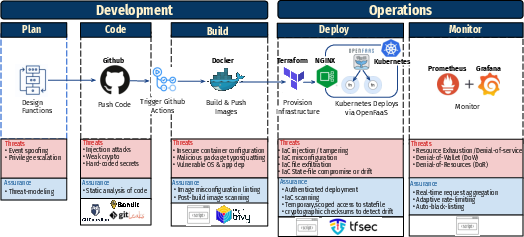
Figure 1: FaaSGardâs DevSecOps pipeline covers Plan, Code, Build, Deploy and Monitor phases, integrating threat modeling, static analysis, signed-image verification, and runtime telemetry to secure OpenFaaS functions end to end.
Implementation on OpenFaaS
The implementation on OpenFaaS uses Python—widely used in serverless functions—and integrates with commodity tooling like GitHub Actions, Docker, and Terraform. Security checkpoints in OpenFaaS's Kubernetes-native ecosystem are empowered by tools like Bandit, Gitleaks, and Trivy, ensuring proactive security measures.
Evaluation Metrics and Results
Development-Phase Evaluation
FaaSGuard was evaluated using real-world OpenFaaS functions sourced from GitHub. The validation demonstrated a high precision of 95% and recall of 91%. Detected vulnerabilities included:
- Vulnerable dependencies (50% of projects).
- Code misconfigurations (20% of projects).
- Plain-text secrets (10% of projects).
These evaluated metrics show strong efficacy in identifying and mitigating security threats at multiple stages, highlighting the utility and robustness of a full-lifecycle approach in mitigating security risks in serverless architectures.
Operation-Phase Evaluation
In testing OpenFaaS applications, FaaSGuard successfully blocked infrastructure misconfigurations (e.g., RBAC wielding and state-file discrepancies) with a negligible impact on deployment latency while maintaining service reliability under adverse traffic conditions. The runtime security effectively mitigated resource-exhaustion attacks and burst traffic with minimal false positives, demonstrating controlled deployment and operational security without impeding performance.
Conclusion
FaaSGuard exemplifies how comprehensive DevSecOps can be effectively realized in serverless environments, addressing critical security challenges specific to open-source platforms. It strikes a balance between stringent security and operational practicality, achieving significant mitigation of serverless-related vulnerabilities without derailing CI/CD efficacy.
Future work may focus on expanding FaaSGuard's language applicability beyond Python and enhancing adaptive policies for dynamic thresholds in security monitoring, thereby increasing the generalizability and efficiency of its deployment across diverse serverless architectures.
