SoK: Comprehensive Analysis of Rug Pull Causes, Datasets, and Detection Tools in DeFi (2403.16082v1)
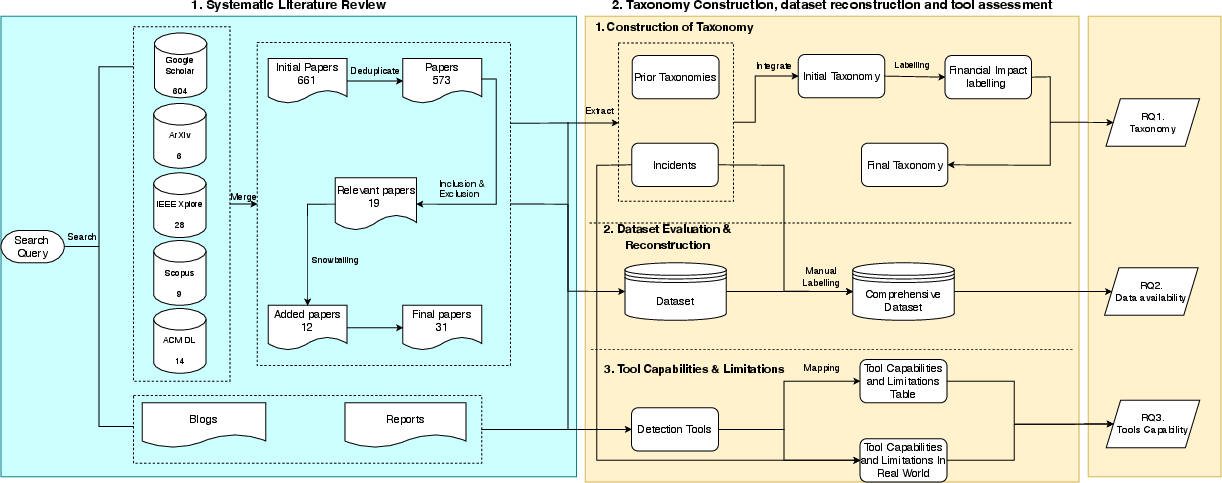
Abstract: Rug pulls pose a grave threat to the cryptocurrency ecosystem, leading to substantial financial loss and undermining trust in decentralized finance (DeFi) projects. With the emergence of new rug pull patterns, research on rug pull is out of state. To fill this gap, we first conducted an extensive analysis of the literature review, encompassing both scholarly and industry sources. By examining existing academic articles and industrial discussions on rug pull projects, we present a taxonomy inclusive of 34 root causes, introducing six new categories inspired by industry sources: burn, hidden owner, ownership transfer, unverified contract, external call, and fake LP lock. Based on the developed taxonomy, we evaluated current rug pull datasets and explored the effectiveness and limitations of existing detection mechanisms. Our evaluation indicates that the existing datasets, which document 2,448 instances, address only 7 of the 34 root causes, amounting to a mere 20% coverage. It indicates that existing open-source datasets need to be improved to study rug pulls. In response, we have constructed a more comprehensive dataset containing 2,360 instances, expanding the coverage to 54% with the best effort. In addition, the examination of 14 detection tools showed that they can identify 25 of the 34 root causes, achieving a coverage of 73.5%. There are nine root causes (Fake LP Lock, Hidden Fee, and Destroy Token, Fake Money Transfer, Ownership Transfer, Liquidity Pool Block, Freeze Account, Wash-Trading, Hedge) that the existing tools cannot cover. Our work indicates that there is a significant gap between current research and detection tools, and the actual situation of rug pulls.
- B. Mazorra, V. Adan, and V. Daza, “Do not rug on me: Leveraging machine learning techniques for automated scam detection,” Mathematics, vol. 10, no. 6, p. 949, 2022.
- J. G. Botha, D. P. Botha-Badenhorst, and L. Leenen, “An analysis of crypto scams during the covid-19 pandemic: 2020-2022,” in Proceedings of the 18th International Conference on Cyber Warfare and Security, 2023. [Online]. Available: http://hdl.handle.net/10204/12898
- M. H. Nguyen, P. D. Huynh, S. H. Dau, and X. Li, “Rug-pull malicious token detection on blockchain using supervised learning with feature engineering,” in Proceedings of the 2023 Australasian Computer Science Week, 2023, pp. 72–81.
- N. Aliyev, I. Allahverdiyeva, and T. J. Putniņš, “Scam alert: Can cryptocurrency scams be detected early?” Available at SSRN 4490180, 2023.
- P. D. Huynh, T. De Silva, S. H. Dau, X. Li, I. Gondal, and E. Viterbo, “From programming bugs to multimillion-dollar scams: An analysis of trapdoor tokens on decentralized exchanges,” arXiv preprint arXiv:2309.04700, 2023.
- S. Kaur, S. Singh, S. Gupta, and S. Wats, “Risk analysis in decentralized finance (defi): a fuzzy-ahp approach,” Risk Management, vol. 25, no. 2, p. 13, 2023.
- M. Cao, Y. Zhang, Z. Feng, J. Hu, and Y. Zhu, “Tokenauditor: Detecting manipulation risk in token smart contract by fuzzing,” in 2022 IEEE 22nd International Conference on Software Quality, Reliability and Security (QRS). IEEE, 2022, pp. 651–662.
- J. Huang, N. He, K. Ma, J. Xiao, and H. Wang, “A deep dive into nft rug pulls,” arXiv preprint arXiv:2305.06108, 2023.
- Etherscan, “Doge3.0,” https://etherscan.io/token/0x820ba67398c3ea745eb8766fd3f444a92d4de316, 2023, accessed: 30-Sept-2023.
- B. Kitchenham, O. P. Brereton, D. Budgen, M. Turner, J. Bailey, and S. Linkman, “Systematic literature reviews in software engineering–a systematic literature review,” Information and software technology, vol. 51, no. 1, pp. 7–15, 2009.
- V. Garousi, M. Felderer, and M. V. Mäntylä, “Guidelines for including grey literature and conducting multivocal literature reviews in software engineering,” Information and software technology, vol. 106, pp. 101–121, 2019.
- S. Nakamoto, “Bitcoin: A peer-to-peer electronic cash system,” SSRN: 3440802, 2008, available at SSRN: https://ssrn.com/abstract=3440802.
- P. Xia, H. Wang, B. Gao, W. Su, Z. Yu, X. Luo, C. Zhang, X. Xiao, and G. Xu, “Trade or trick? detecting and characterizing scam tokens on uniswap decentralized exchange,” Proceedings of the ACM on Measurement and Analysis of Computing Systems, vol. 5, no. 3, pp. 1–26, 2021.
- F. Cernera, M. La Morgia, A. Mei, and F. Sassi, “Token spammers, rug pulls, and sniper bots: An analysis of the ecosystem of tokens in ethereum and in the binance smart chain ({{\{{{{\{{{{\{{{{\{{{{\{{BNB}}\}}}}\}}}}\}}}}\}}}}\}}),” in 32nd USENIX Security Symposium (USENIX Security 23), 2023, pp. 3349–3366.
- “DeFi Rekt Database,” https://de.fi/rekt-database, accessed: 30-Sept-2023.
- Nina Semczuk, “What is a rug pull?” https://www.bankrate.com/investing/what-is-a-rug-pull/, 2023, accessed: 30-Sept-2023.
- Hacken, “Rug pull explained,” https://hacken.io/discover/rug-pull-explained/, 2023, accessed: 30-Sept-2023.
- Andy Rosen, Dalia Ramirez, “What is a rug pull?” https://www.nerdwallet.com/article/investing/rug-pull, 2023, accessed: 30-Sept-2023.
- “Crypto defi rug pull: How to spot,” https://www.immunebytes.com/blog/crypto-defi-rug-pull-how-to-spot/#Liquidity_Stealing, 2023, accessed: 30-Sept-2023.
- B. Becher, “What exactly is a rug pull?” https://builtin.com/blockchain-cryptocurrency-finance-fintech/what-rug-pull-exactly, 2023, accessed: 30-Sept-2023.
- C. Vantage, “What are the biggest crypto rug pulls in history?” https://www.cryptovantage.com/news/what-are-the-biggest-crypto-rug-pulls-in-history/, 2023, accessed: 30-Sept-2023.
- Z. Vardai, “How to avoid getting rug pull scammed in crypto and defi,” https://forkast.news/how-avoid-getting-rug-pull-scammed-crypto-defi/, 2023, accessed: 30-Sept-2023.
- Numen, “Rug pulls in cryptocurrency,” https://www.numencyber.com/rug-pulls-in-cryptocurrency/, 2023, accessed: 30-Sept-2023.
- Becky, “The different types of rug pulls in cryptocurrency scams,” https://www.coininsider.com/the-different-types-of-rug-pulls-in-cryptocurrency-scams/, 2023, accessed: 30-Sept-2023.
- CryptoAdventure, “Slow rug pulls: The wild nature of cryptocurrency projects,” https://hackernoon.com/slow-rug-pulls-the-wild-nature-of-cryptocurrency-projects, 2023, accessed: 30-Sept-2023.
- “Rug pulls – red flags to look out for,” https://frontal.io/rugpull/, 2023, accessed: 30-Sept-2023.
- ApeSpace, “What is a rug pull? the latest cryptocurrency scam,” https://apespace.io/learn/what-is-a-rug-pull-the-latest-cryptocurrency-scam/, 2023, accessed: 30-Sept-2023.
- C. Austin, “Defi top 10 list of crypto rug pulls,” https://coinscreed.com/defi-top-10-list-of-crypto-rug-pulls.html, 2023, accessed: 30-Sept-2023.
- F. Corva, “What is a crypto rug pull?” https://www.finder.com/cryptocurrency/what-is-a-crypto-rug-pull, 2023, accessed: 30-Sept-2023.
- “Rug pull due diligence services,” https://www.quillaudits.com/services/rug-pull-due-diligence-services, 2023, accessed: 30-Sept-2023.
- “The rug pull report,” https://www.certik.com/resources/blog/5Zai85KkvIgW0wBJPQxl3i-the-rug-pull-report, 2023, accessed: 30-Sept-2023.
- F. Ma, M. Ren, L. Ouyang, Y. Chen, J. Zhu, T. Chen, Y. Zheng, X. Dai, Y. Jiang, and J. Sun, “Pied-piper: Revealing the backdoor threats in ethereum erc token contracts,” ACM Transactions on Software Engineering and Methodology, vol. 32, no. 3, pp. 1–24, 2023.
- C. F. Tuan Phan, “Mapping a serial rug pull scammer on binance smart chain,” https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2022/mapping-a-serial-rug-pull-scammer-on-binance-smart-chain, 2022, accessed: 30-Sept-2023.
- O. V. Dikla Barda, Roman Zaikin, “Scammers are creating new fraudulent crypto tokens and misconfiguring smart contracts to steal funds,” https://research.checkpoint.com/2022/scammers-are-creating-new-fraudulent-crypto-tokens-and-misconfiguring-smart-contracts-to-steal-funds/, 2022, accessed: 30-Sept-2023.
- QuillAudits, “Analyzing backdoors in scam token contracts: Quillaudits,” https://quillaudits.medium.com/analyzing-backdoors-in-scam-token-contracts-quillaudits-d426c06199bb, 2023, accessed: 30-Sept-2023.
- S. Labs, “Rug pull report 2022,” https://www.soliduslabs.com/reports/rug-pull-report, Solidus Labs, Tech. Rep., 2023, accessed: 30-Sept-2023.
- U. Support, “Unsellable token scams,” https://support.uniswap.org/hc/en-us/articles/17523088290573-Unsellable-token-scams, accessed: 30-Sept-2023.
- C. F. Torres, M. Steichen et al., “The art of the scam: Demystifying honeypots in ethereum smart contracts,” in 28th USENIX Security Symposium (USENIX Security 19), 2019, pp. 1591–1607.
- R. Gan, L. Wang, and X. Lin, “Why trick me: The honeypot traps on decentralized exchanges,” in Proceedings of the 2023 Workshop on Decentralized Finance and Security, 2023, pp. 17–23.
- “Defi cryptocurrency rug pulls,” https://www.cybertalk.org/2021/09/02/defi-cryptocurrency-rug-pulls/, 2021, accessed: 30-Sept-2023.
- M. Norouzi, M. Elgharabawy, and K. Zhang, “The greed trap: Uncovering intrinsic ethereum honeypots through symbolic execution,” in 2023 Fifth International Conference on Blockchain Computing and Applications (BCCA). IEEE, 2023, pp. 440–447.
- A. M. O., “Rug pull: How to spot the fraud easily via smart contract codes,” Coinsbench, 2022, accessed: 30-Sept-2023.
- De.Fi Rekt Database, “Analysis of 0xdc2ce29256a7f44c3a291f8c08d575593455bc39 incident,” https://de.fi/rekt-database/0xdc2ce29256a7f44c3a291f8c08d575593455bc39, accessed: 30-Sept-2023.
- Shashank, “Circulatebusd hack analysis: Have you ever been rug pulled?” SolidityScan Blog, 2023, accessed: 30-Sept-2023. [Online]. Available: https://blog.solidityscan.com/circulatebusd-hack-analysis-have-you-ever-been-rug-pulled-cca36c1dc4f5
- S. Dos Santos, J. Singh, R. K. Thulasiram, S. Kamali, L. Sirico, and L. Loud, “A new era of blockchain-powered decentralized finance (defi)-a review,” in 2022 IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC). IEEE, 2022, pp. 1286–1292.
- Ancilia, “The uniswap skim token balance attack,” https://medium.com/@Ancilia/the-uniswap-skim-token-balance-attack-b1399943d560, 2023, accessed: 30-Sept-2023.
- CertiKAlert, “Fake lp lock rug pull incident,” 2023, twitter post. Retrieved from https://twitter.com/CertiKAlert/status/1716554530010157508.
- J. Xu, K. Paruch, S. Cousaert, and Y. Feng, “Sok: Decentralized exchanges (dex) with automated market maker (amm) protocols,” ACM Computing Surveys, vol. 55, no. 11, pp. 1–50, 2023.
- QuillAudit, “Analyzing backdoors in scam token contracts,” https://quillaudits.medium.com/analyzing-backdoors-in-scam-token-contracts-quillaudits-d426c06199bb, 2022, accessed: 30-Sept-2023.
- T. Phan and C. Friedman, “Mapping a serial rug pull scammer on binance smart chain,” https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2022/mapping-a-serial-rug-pull-scammer-on-binance-smart-chain, 2022, accessed: 30-Sept-2023.
- QuillAudits, “Analyzing backdoors in scam token contracts,” Medium, 2022, accessed: 30-Sept-2023. [Online]. Available: https://quillaudits.medium.com/analyzing-backdoors-in-scam-token-contracts-quillaudits-d426c06199bb
- “Rug pull dataset,” https://github.com/Dianxiang111/Rug-Pull-Dataset, 2024, accessed: 2024-03-22.
- T. Sharma, R. Agarwal, and S. K. Shukla, “Understanding rug pulls: an in-depth behavioral analysis of fraudulent nft creators,” ACM Transactions on the Web, vol. 18, no. 1, pp. 1–39, 2023.
- W. Ma, C. Zhu, Y. Liu, X. Xie, and Y. Li, “A comprehensive study of governance issues in decentralized finance applications,” arXiv preprint arXiv:2311.01433, 2023.