- The paper introduces the {
ame} framework, which leverages dynamic instrumentation and whitelisting policies to enforce control flow integrity in smart contracts.
- It validates its approach through empirical analysis of over 1.3 million transactions across 30 DeFi protocols, preventing 28 out of 30 attacks with a 0.28% false positive rate.
- The framework’s real-time defense mechanism highlights practical improvements in smart contract security, critical for complex, composable DeFi ecosystems.
Enhancing Smart Contract Security through Control Flow Integrity
The paper "Secure Smart Contract with Control Flow Integrity" (2504.05509) introduces {\name}, a novel framework designed to bolster the security of smart contracts, particularly within the DeFi ecosystem. This framework addresses the increasing sophistication of attacks by enforcing control flow integrity in real-time, without requiring prior knowledge of specific hacks. Through empirical analysis and dynamic enforcement of control flow whitelisting policies, {\name} offers a robust defense mechanism against evolving threats.
Background and Motivation
The proliferation of DeFi services has made smart contracts a critical component of blockchain technology. However, vulnerabilities in these contracts have led to substantial financial losses, highlighting the need for enhanced security measures. Traditional security approaches often fall short due to the composability of DeFi protocols, where multiple contracts interact in complex ways. This composability allows attackers to exploit unforeseen uses of contracts to orchestrate exploits in ways that developers did not predict. The paper identifies that attack transactions often exhibit novel control flows that deviate from the intended design, prompting the development of {\name} as a solution.
Empirical Study of Control Flows
To understand the nature of attacks, the authors conducted an empirical paper of $1,327,925$ historical transactions across $30$ compromised protocols on Ethereum. The analysis focused on identifying differences between control flows in benign transactions and those in attack transactions.
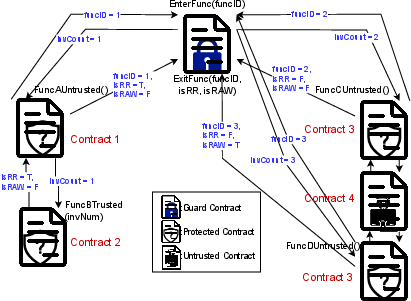
Figure 1: A Running Example of {\name}
The paper revealed that attack transactions frequently introduce unique control flows not previously observed in benign transactions. Specifically, in $24$ out of the $30$ studied hack incidents, the attack transactions demonstrated control flows that were distinct from any previously observed transaction patterns. However, in $6$ cases, involving protocols such as bZx, VisorFi, UmbrellaNetwork, Opyn, DODO and Bedrock_DeFi, the control flows had been observed previously in benign transactions. Further investigation revealed that the UmbrellaNetwork and Bedrock_DeFi hacks were traced back to an integer underflow vulnerability and a price miscalculation issue, respectively, which were executed through one function call to steal funds. The remaining $4$ hacks presented a different complexity and involved various types of re-entrancy attacks. While operating under the guise of familiar top-level function calls, these attacks manifested unique and sophisticated control flows at deeper interaction levels.
The {\name} Framework
The {\name} framework enforces control flow integrity through a combination of instrumentation and dynamic analysis. It consists of the following key components:
- Instrumentation: Existing smart contracts are instrumented with additional code to track control flow data.
- Guard Contract: A new guard contract is deployed to collect control flow data from the instrumented contracts.
- Whitelisting Policies: Four whitelisting policies are enforced at runtime to detect and neutralize attacks that exploit unexpected control flows.
- Simplification Heuristics: Heuristics are applied to simplify the collected control flows and reduce false positives.
Control Flow Whitelisting Policies
{\name} employs four whitelisting policies to identify benign invocations:
- Simple Independent Invocations: An invocation is considered benign if it is simple (does not involve re-entrancy) and independent of any prior invocations within the transaction.
- Read-Only Invocations: An invocation is considered benign if it is read-only and does not modify any blockchain state.
- Runtime Read-Only (RR) Function Calls: A function call is considered runtime read-only if it does not have a storage write (SSTORE) and performs no Ether transfers.
- Restore-on-Exit (RE) Storage Writes: This heuristic permits to safely ignore storage writes that temporarily alter values but restore the original state at the end of execution.
Control Flow Simplification Heuristics
To further reduce complexity and minimize false positives, {\name} implements two heuristics:
- ERC20 Function Calls: Calls to standard ERC20 functions (transfer, transferFrom, approve, increaseAllowance, and decreaseAllowance) are ignored, as they are considered benign and widely used.
- Read-After-Write (RAW) Dependency: An invocation is considered RAW-dependent on an earlier invocation if it reads from a storage location that the earlier invocation wrote to. In the absence of such dependencies, simple invocations are treated as independent.
Implementation Details
The {\name} framework is integrated into a DeFi protocol pre-deployment by instrumenting the original code. The system consists of instrumentation within the protected contracts and a guard contract. Each function in the protected contracts is instrumented and assigned a unique positive integer as its function identifier. When an instrumented function is invoked, it sends the guard contract its identifier to record its function entry and receives a positive integer value indicating the invocation count. The instrumented function then tracks storage accesses, records storage writes using the invocation count, and sends control flow data to the guard contract upon exit. The guard contract collects this control flow data from the protected contracts, simplifies it using the defined heuristics, evaluates whether the control flow is whitelisted, and reverts the transaction if it is not.
Experimental Results
The authors evaluated {\name} on the deployed smart contracts and their transactions of the $30$ DeFi protocols included in their empirical paper. The results indicate that, when configured only once before deployment, {\name} can effectively prevent $28$ out of $30$ attacks analyzed in the paper, maintaining a low average false positive rate of just 0.28%. Further experiments were performed under extreme conditions by applying {\name} to another $3$ widely adopted DeFi protocolsâAAVE, Lido, and Uniswap. The experimental results demonstrated that {\name} maintained a low false positive rate under real-world extreme conditions.
Contributions and Significance
The key contributions of this paper are:
- An empirical paper of control flows in historical transactions of compromised DeFi protocols, uncovering critical insights into control flow patterns and DeFi composability.
- The {\name} technique, which introduces control flow integrity for smart contracts through whitelisting policies and simplification heuristics.
- An evaluation of {\name}'s effectiveness in preventing attacks, with open access to paper results, experimental data, and the tool itself.
The {\name} framework represents a significant advancement in smart contract security by providing a dynamic, real-time defense against complex attacks. Its ability to operate without prior knowledge of specific hacks makes it particularly valuable in the rapidly evolving DeFi landscape.
Conclusion
The {\name} framework offers a practical and effective approach to enhancing smart contract security within the DeFi ecosystem. By dynamically enforcing control flow integrity, {\name} mitigates a wide range of sophisticated attacks while maintaining a low false positive rate and manageable gas overhead. The insights from this research contribute to the ongoing development of more secure and resilient DeFi protocols.
