A Survey on Decentralized Identifiers and Verifiable Credentials
Abstract: Digital identity has always been considered the keystone for implementing secure and trustworthy communications among parties. The ever-evolving digital landscape has gone through many technological transformations that have also affected the way entities are digitally identified. During this digital evolution, identity management has shifted from centralized to decentralized approaches. The last era of this journey is represented by the emerging Self-Sovereign Identity (SSI), which gives users full control over their data. SSI leverages decentralized identifiers (DIDs) and verifiable credentials (VCs), which have been recently standardized by the World Wide Web Community (W3C). These technologies have the potential to build more secure and decentralized digital identity systems, remarkably contributing to strengthening the security of communications that typically involve many distributed participants. It is worth noting that the scope of DIDs and VCs extends beyond individuals, encompassing a broad range of entities including cloud, edge, and Internet of Things (IoT) resources. However, due to their novelty, existing literature lacks a comprehensive survey on how DIDs and VCs have been employed in different application domains, which go beyond SSI systems. This paper provides readers with a comprehensive overview of such technologies from different perspectives. Specifically, we first provide the background on DIDs and VCs. Then, we analyze available implementations and offer an in-depth review of how these technologies have been employed across different use-case scenarios. Furthermore, we examine recent regulations and initiatives that have been emerging worldwide. Finally, we present some challenges that hinder their adoption in real-world scenarios and future research directions.
- P. A. Grassi, M. E. Garcia, and J. L. Fenton, “Digital identity guidelines,” NIST special publication, vol. 800, pp. 63–3, 2017.
- K.-Y. Lam and C.-H. Chi, “Identity in the Internet-of-Things (IoT): New Challenges and Opportunities,” in Information and Communications Security, K.-Y. Lam, C.-H. Chi, and S. Qing, Eds. Cham: Springer International Publishing, 2016, pp. 18–26.
- K. Shafique, B. A. Khawaja, F. Sabir, S. Qazi, and M. Mustaqim, “Internet of Things (IoT) for Next-Generation Smart Systems: A Review of Current Challenges, Future Trends and Prospects for Emerging 5G-IoT Scenarios,” IEEE Access, vol. 8, pp. 23 022–23 040, 2020.
- M. A. Olivero, A. Bertolino, F. J. Domínguez-Mayo, M. J. Escalona, and I. Matteucci, “Digital persona portrayal: Identifying pluridentity vulnerabilities in digital life,” Journal of Information Security and Applications, vol. 52, p. 102492, 2020.
- S. Alneyadi, E. Sithirasenan, and V. Muthukkumarasamy, “A survey on data leakage prevention systems,” Journal of Network and Computer Applications, vol. 62, pp. 137–152, 2016.
- D. Silver, S. Jana, D. Boneh, E. Chen, and C. Jackson, “Password Managers: Attacks and Defenses,” in 23rd USENIX Security Symposium (USENIX Security 14). San Diego, CA: USENIX Association, Aug. 2014, pp. 449–464. [Online]. Available: https://www.usenix.org/conference/usenixsecurity14/technical-sessions/presentation/silver
- K. Thomas, J. Pullman, K. Yeo, A. Raghunathan, P. G. Kelley, L. Invernizzi, B. Benko, T. Pietraszek, S. Patel, D. Boneh, and E. Bursztein, “Protecting accounts from credential stuffing with password breach alerting,” in 28th USENIX Security Symposium (USENIX Security 19). Santa Clara, CA: USENIX Association, Aug. 2019, pp. 1556–1571. [Online]. Available: https://www.usenix.org/conference/usenixsecurity19/presentation/thomas
- P. C. Bartolomeu, E. Vieira, S. M. Hosseini, and J. Ferreira, “Self-Sovereign Identity: Use-cases, Technologies, and Challenges for Industrial IoT,” in 2019 24th IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), 2019, pp. 1173–1180.
- M. Alizadeh, K. Andersson, and O. Schelén, “Comparative Analysis of Decentralized Identity Approaches,” IEEE Access, vol. 10, pp. 92 273–92 283, 2022.
- EU, “Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation),” 2016. [Online]. Available: https://eur-lex.europa.eu/eli/reg/2016/679/oj/eng
- A. Mühle, A. Grüner, T. Gayvoronskaya, and C. Meinel, “A survey on essential components of a self-sovereign identity,” Computer Science Review, vol. 30, pp. 80–86, 2018.
- N. Romandini, A. Mora, C. Mazzocca, R. Montanari, and P. Bellavista, “Federated Unlearning: A Survey on Methods, Design Guidelines, and Evaluation Metrics,” arXiv preprint arXiv:2401.05146, 2024.
- W3 Recommendation, “Decentralized Identifiers (DIDs) v1.0,” 2022. [Online]. Available: https://www.w3.org/TR/did-core/
- W. Recommendation, “Verifiable Credentials Data Model v1.1,” 2022. [Online]. Available: https://www.w3.org/TR/vc-data-model/
- S. Cucko and M. Turkanović, “Decentralized and Self-Sovereign Identity: Systematic Mapping Study,” IEEE Access, vol. 9, pp. 139 009–139 027, 2021.
- R. Soltani, U. T. Nguyen, and A. An, “A Survey of Self-Sovereign Identity Ecosystem,” Security and Communication Networks, vol. 2021, p. 8873429, Jul 2021.
- Y. Bai, H. Lei, S. Li, H. Gao, J. Li, and L. Li, “Decentralized and Self-Sovereign Identity in the Era of Blockchain: A Survey,” in 2022 IEEE International Conference on Blockchain (Blockchain), 2022, pp. 500–507.
- F. Schardong and R. Custódio, “Self-sovereign identity: A systematic review, mapping and taxonomy,” Sensors, vol. 22, no. 15, 2022.
- M. Davie, D. Gisolfi, D. Hardman, J. Jordan, D. O’Donnell, and D. Reed, “The Trust over IP Stack,” IEEE Communications Standards Magazine, vol. 3, no. 4, pp. 46–51, 2019.
- European Union, “ Regulation of the European Parliament and of The Council Amending Regulation (Eu) No 910/2014 as Regards Establishing a Framework for a European Digital Identity,” 2021. [Online]. Available: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX:52021PC0281
- T. El Maliki and J.-M. Seigneur, “A Survey of User-centric Identity Management Technologies,” in The International Conference on Emerging Security Information, Systems, and Technologies (SECUREWARE 2007), 2007, pp. 12–17.
- A. Pérez-Méndez, F. Pereñíguez-García, R. Marín-López, G. López-Millán, and J. Howlett, “Identity Federations Beyond the Web: A Survey,” IEEE Communications Surveys & Tutorials, vol. 16, no. 4, pp. 2125–2141, 2014.
- J. Torres, M. Nogueira, and G. Pujolle, “A Survey on Identity Management for the Future Network,” IEEE Communications Surveys & Tutorials, vol. 15, no. 2, pp. 787–802, 2013.
- Y. Liu, D. He, M. S. Obaidat, N. Kumar, M. K. Khan, and K.-K. Raymond Choo, “Blockchain-based identity management systems: A review,” Journal of Network and Computer Applications, vol. 166, p. 102731, 2020.
- L. Ante, C. Fischer, and E. Strehle, “A bibliometric review of research on digital identity: Research streams, influential works and future research paths,” Journal of Manufacturing Systems, vol. 62, pp. 523–538, 2022.
- D. Pöhn and W. Hommel, “An Overview of Limitations and Approaches in Identity Management,” in Proceedings of the 15th International Conference on Availability, Reliability and Security, ser. ARES ’20. New York, NY, USA: Association for Computing Machinery, 2020.
- M. Yıldırım and I. Mackie, “Encouraging users to improve password security and memorability,” International Journal of Information Security, vol. 18, no. 6, pp. 741–759, Dec 2019.
- D. Zhe, W. Qinghong, S. Naizheng, and Z. Yuhan, “Study on Data Security Policy Based on Cloud Storage,” in 2017 ieee 3rd international conference on big data security on cloud (bigdatasecurity), ieee international conference on high performance and smart computing (hpsc), and ieee international conference on intelligent data and security (ids), 2017, pp. 145–149.
- A. Armando, R. Carbone, L. Compagna, J. Cuellar, and L. Tobarra, “Formal Analysis of SAML 2.0 Web Browser Single Sign-on: Breaking the SAML-Based Single Sign-on for Google Apps,” in Proceedings of the 6th ACM Workshop on Formal Methods in Security Engineering, ser. FMSE ’08. New York, NY, USA: Association for Computing Machinery, 2008, p. 1–10.
- A. A. Malik, H. Anwar, and M. A. Shibli, “Federated Identity Management (FIM): Challenges and opportunities,” in 2015 Conference on Information Assurance and Cyber Security (CIACS), 2015, pp. 75–82.
- R. Laborde, A. Oglaza, S. Wazan, F. Barrere, A. Benzekri, D. W. Chadwick, and R. Venant, “A User-Centric Identity Management Framework based on the W3C Verifiable Credentials and the FIDO Universal Authentication Framework,” in 2020 IEEE 17th Annual Consumer Communications & Networking Conference (CCNC), 2020, pp. 1–8.
- D. Recordon and D. Reed, “OpenID 2.0: A Platform for User-Centric Identity Management,” in Proceedings of the Second ACM Workshop on Digital Identity Management, ser. DIM ’06. New York, NY, USA: Association for Computing Machinery, 2006, p. 11–16.
- S. Srinivas, D. Balfanz, E. Tiffany, A. Czeskis, and F. Alliance, “Universal 2nd factor (U2F) overview,” FIDO Alliance Proposed Standard, vol. 15, 2015.
- D. Hardt, “The OAuth 2.0 authorization framework,” Tech. Rep., 2012.
- A. Jøsang, C. Rosenberger, L. Miralabé, H. Klevjer, K. A. Varmedal, J. Daveau, K. E. Husa, and P. Taugbøl, “Local user-centric identity management,” Journal of Trust Management, vol. 2, no. 1, p. 1, Jan 2015. [Online]. Available: https://doi.org/10.1186/s40493-014-0009-6
- A. Tobin and D. Reed, “The inevitable rise of self-sovereign identity,” The Sovrin Foundation, vol. 29, no. 2016, p. 18, 2016.
- M. S. Ferdous, F. Chowdhury, and M. O. Alassafi, “In Search of Self-Sovereign Identity Leveraging Blockchain Technology,” IEEE Access, vol. 7, pp. 103 059–103 079, 2019.
- W. Recommendation, “World Wide Web Consortium,” 2021. [Online]. Available: https://www.w3.org/
- I. Foundation, “Peer DID Method Specification,” 2021. [Online]. Available: https://identity.foundation/peer-did-method-spec/
- M. Sabadello, “A universal resolver for self-sovereign identifiers,” Decentralized Identity Foundation, 2017.
- B. Alangot, P. Szalachowski, T. T. A. Dinh, S. Meftah, J. I. Gana, K. M. M. Aung, and Z. Li, “Decentralized Identity Authentication with Auditability and Privacy,” Algorithms, vol. 16, no. 1, 2023.
- M. Sabadello, K. Den Hartog, C. Lundkvist, C. Franz, A. Elias, A. Hughes, J. Jordan, and D. Zagidulin, “Introduction to did auth,” Rebooting the Web of Trust VI, 2018.
- M. Alizadeh, K. Andersson, and O. Schelén, “Performance Analysis of Verifiable Data Registry Solutions for Decentralized Identifiers,” in 2022 IEEE Asia-Pacific Conference on Computer Science and Data Engineering (CSDE), 2022, pp. 1–8.
- J. García-Rodríguez, R. Torres Moreno, J. Bernal Bernabé, and A. Skarmeta, “Towards a Standardized Model for Privacy-Preserving Verifiable Credentials,” in Proceedings of the 16th International Conference on Availability, Reliability and Security, ser. ARES ’21. New York, NY, USA: Association for Computing Machinery, 2021.
- P. Dunphy and F. A. Petitcolas, “A First Look at Identity Management Schemes on the Blockchain,” IEEE Security & Privacy, vol. 16, no. 4, pp. 20–29, 2018.
- W. Zou, D. Lo, P. S. Kochhar, X.-B. D. Le, X. Xia, Y. Feng, Z. Chen, and B. Xu, “Smart Contract Development: Challenges and Opportunities,” IEEE Transactions on Software Engineering, vol. 47, no. 10, pp. 2084–2106, 2021.
- B. Alzahrani, “An Information-Centric Networking Based Registry for Decentralized Identifiers and Verifiable Credentials,” IEEE Access, vol. 8, pp. 137 198–137 208, 2020.
- DIDKit, “DIDKit.” [Online]. Available: https://www.spruceid.dev/didkit/didkit
- I. Fundation, “IOTA Identity Framework.” [Online]. Available: https://github.com/iotaledger/identity.rs
- Hyperledger, “Hyperledger Aries.” [Online]. Available: https://www.hyperledger.org/projects/aries
- Microsoft, “Microsoft Entra Wallet Library.” [Online]. Available: https://github.com/microsoft/entra-verifiedid-wallet-library-ios#microsoft-entra-wallet-library
- Veramo, “Veramo.” [Online]. Available: https://veramo.io/
- I. Agudo, M. Montenegro-Gómez, and J. Lopez, “A Blockchain Approach for Decentralized V2X (D-V2X),” IEEE Transactions on Vehicular Technology, vol. 70, no. 5, pp. 4001–4010, 2021.
- P. Michalopoulos, J. Meijers, S. F. Singh, and A. Veneris, “A V2X Reputation System with Privacy Considerations,” in 2022 IEEE 13th International Conference on Software Engineering and Service Science (ICSESS), 2022, pp. 8–14.
- X. Li, T. Jing, R. Li, H. Li, X. Wang, and D. Shen, “BDRA: Blockchain and Decentralized Identifiers Assisted Secure Registration and Authentication for VANETs,” IEEE Internet of Things Journal, pp. 1–1, 2022.
- P. C. Bartolomeu, J. Bernardino, and J. Ferreira, “Decentralized Ad-Hoc Seaport Truck Authentication,” in 2022 IEEE 19th Annual Consumer Communications & Networking Conference (CCNC), 2022, pp. 417–420.
- S. Terzi, C. Savvaidis, A. Sersemis, K. Votis, and D. Tzovaras, “Decentralizing Identity Management and Vehicle Rights Delegation through Self-Sovereign Identities and Blockchain,” in 2021 IEEE 45th Annual Computers, Software, and Applications Conference (COMPSAC), 2021, pp. 1217–1223.
- D. Wilms, C. Stoecker, and J. Caballero, “Data Provenance in Vehicle Data Chains,” in 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-Spring), 2021, pp. 1–5.
- N. Prakash, D. G. Michelson, and C. Feng, “CVIN: Connected Vehicle Information Network,” in 2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring), 2020, pp. 1–6.
- M. Kim, J. Lee, J. Oh, K. Park, Y. Park, and K. Park, “Blockchain based energy trading scheme for vehicle-to-vehicle using decentralized identifiers,” Applied Energy, vol. 322, p. 119445, 2022.
- R. P. Parameswarath, P. Gope, and B. Sikdar, “User-empowered privacy-preserving authentication protocol for electric vehicle charging based on decentralized identity and verifiable credential,” ACM Trans. Manage. Inf. Syst., vol. 13, no. 4, aug 2022.
- S. Di Martino, E. Landolfi, N. Mazzocca, F. Rocco di Torrepadula, and L. L. L. Starace, “A visual-based toolkit to support mobility data analytics,” Expert Systems with Applications, vol. 238, p. 121949, 2024.
- A. Feraudo, A. Calvio, A. Bujari, and P. Bellavista, “A Novel Design for Advanced 5G Deployment Environments with Virtualized Resources at Vehicular and MEC Nodes,” in 2023 IEEE Vehicular Networking Conference (VNC), 2023, pp. 97–103.
- “ Mobility Open Blocjchain Initative (MOBI).” [Online]. Available: https://dlt.mobi/
- M. Campaña, E. Inga, and J. Cárdenas, “Optimal Sizing of Electric Vehicle Charging Stations Considering Urban Traffic Flow for Smart Cities,” Energies, vol. 14, no. 16, 2021.
- M. Eisenstadt, M. Ramachandran, N. Chowdhury, A. Third, and J. Domingue, “COVID-19 Antibody Test/Vaccination Certification: There’s an App for That,” IEEE Open Journal of Engineering in Medicine and Biology, vol. 1, pp. 148–155, 2020.
- A. Abid, S. Cheikhrouhou, S. Kallel, and M. Jmaiel, “NovidChain: Blockchain-based privacy-preserving platform for COVID-19 test/vaccine certificates,” Software: Practice and Experience, vol. 52, no. 4, pp. 841–867, 2022.
- M. Abubakar, P. McCarron, Z. Jaroucheh, A. Al Dubai, and B. Buchanan, “Blockchain-based Platform for Secure Sharing and Validation of Vaccination Certificates,” in 2021 14th International Conference on Security of Information and Networks (SIN), vol. 1, 2021, pp. 1–8.
- F. A. Rafid, E. Benissan, L. Murr, I. Ermakov, K. Oikonomou, and P. Zhang, “A Decentralized Identity System for Accelerating Medical Communications within Rare Disease Communities,” in 2022 IEEE International Conference on Blockchain, Smart Healthcare and Emerging Technologies (SmartBlock4Health), 2022, pp. 1–8.
- H. Saidi, N. Labraoui, A. A. A. Ari, L. A. Maglaras, and J. H. M. Emati, “Dsmac: Privacy-aware decentralized self-management of data access control based on blockchain for health data,” IEEE Access, vol. 10, pp. 101 011–101 028, 2022.
- H. Kasyap and S. Tripathy, “Privacy-Preserving Decentralized Learning Framework for Healthcare System,” ACM Trans. Multimedia Comput. Commun. Appl., vol. 17, no. 2s, jun 2021.
- A. M. Alnour and K. H. Kim, “Decentralized Identifiers (DIDs)-Based Authentication Scheme for Smart Health Care System,” in 2022 Thirteenth International Conference on Ubiquitous and Future Networks (ICUFN), 2022, pp. 443–438.
- D. Yoon, S. Moon, K. Park, and S. Noh, “Blockchain-based Personal Data Trading System using Decentralized Identifiers and Verifiable Credentials,” in 2021 International Conference on Information and Communication Technology Convergence (ICTC), 2021, pp. 150–154.
- Z. Wang, Z. Yang, and T. Dong, “A Review of Wearable Technologies for Elderly Care that Can Accurately Track Indoor Position, Recognize Physical Activities and Monitor Vital Signs in Real Time,” Sensors, vol. 17, no. 2, 2017.
- P. Bellavista, L. Foschini, and A. Mora, “Decentralised Learning in Federated Deployment Environments: A System-Level Survey,” ACM Comput. Surv., vol. 54, no. 1, feb 2021.
- P. Gope and T. Hwang, “BSN-Care: A secure IoT-based modern healthcare system using body sensor network,” IEEE sensors journal, vol. 16, no. 5, pp. 1368–1376, 2015.
- L. Patera, A. Garbugli, A. Bujari, D. Scotece, and A. Corradi, “A Layered Middleware for OT/IT Convergence to Empower Industry 5.0 Applications,” Sensors, vol. 22, no. 1, 2022.
- B.-h. Li, B.-c. Hou, W.-t. Yu, X.-b. Lu, and C.-w. Yang, “Applications of artificial intelligence in intelligent manufacturing: a review,” Frontiers of Information Technology & Electronic Engineering, vol. 18, no. 1, pp. 86–96, Jan 2017.
- A. Sghaier Omar and O. Basir, “Decentralized Identifiers and Verifiable Credentials for Smartphone Anticounterfeiting and Decentralized IMEI Database,” Canadian Journal of Electrical and Computer Engineering, vol. 43, no. 3, pp. 174–180, 2020.
- R. Ansey, J. Kempf, O. Berzin, C. Xi, and I. Sheikh, “Gnomon: Decentralized Identifiers for Securing 5G Iot Device Registration and Software Update,” in 2019 IEEE Globecom Workshops (GC Wkshps), 2019, pp. 1–6.
- G. Pescetelli, L. Petrosino, S. D. Valle, G. Ronga, M. Merone, and L. Vollero, “Framework for IoT ecosystems based on distributed ledger technologies and decentralized identifiers,” in 2022 IEEE International Workshop on Metrology for Industry 4.0 & IoT (MetroInd4.0&IoT), 2022, pp. 87–91.
- C. Mazzocca, N. Romandini, M. Mendula, R. Montanari, and P. Bellavista, “TruFLaaS: Trustworthy Federated Learning as a Service,” IEEE Internet of Things Journal, pp. 1–1, 2023.
- P. Bellavista, L. Foschini, R. Montanari, and N. Romandini, “FlowChain: The Playground for Federated Learning in Industrial Internet of Things Environments,” IEEE Internet of Things Magazine, vol. 5, no. 2, pp. 78–83, 2022.
- Y. Li, W. Yang, P. He, C. Chen, and X. Wang, “Design and management of a distributed hybrid energy system through smart contract and blockchain,” Applied Energy, vol. 248, pp. 390–405, 2019.
- S. Hartnett, J. Morris, and I. Vlachos, “Chapter 16 - EW Flex: A decentralized flexibility marketplace fostering TSO-DSO cooperation,” in Mathematical Modelling of Contemporary Electricity Markets, A. Dagoumas, Ed. Academic Press, 2021, pp. 279–286.
- B. Kim, W. Shin, D.-Y. Hwang, and K.-H. Kim, “Attribute-Based Access Control(ABAC) with Decentralized Identifier in the Blockchain-Based Energy Transaction Platform,” in 2021 International Conference on Information Networking (ICOIN), 2021, pp. 845–848.
- M. T., K. Makkithaya, and N. V.G., “A trusted IoT data sharing and secure oracle based access for agricultural production risk management,” Computers and Electronics in Agriculture, vol. 204, p. 107544, 2023.
- L. Cocco, R. Tonelli, and M. Marchesi, “Blockchain and Self Sovereign Identity to Support Quality in the Food Supply Chain,” Future Internet, vol. 13, no. 12, 2021.
- Y. Mezquita, B. Podgorelec, A. B. Gil-González, and J. M. Corchado, “Blockchain-Based Supply Chain Systems, Interoperability Model in a Pharmaceutical Case Study,” Sensors, vol. 23, no. 4, 2023.
- B. Xia, D. Zhang, Y. Liu, Q. Lu, Z. Xing, and L. Zhu, “Trust in Software Supply Chains: Blockchain-Enabled SBOM and the AIBOM Future,” arXiv preprint arXiv:2307.02088, 2023.
- R. Venanzi, S. Dahdal, M. Solimando, L. Campioni, A. Cavalucci, M. Govoni, M. Tortonesi, L. Foschini, L. Attana, M. Tellarini, and C. Stefanelli, “Enabling adaptive analytics at the edge with the Bi-Rex Big Data platform,” Computers in Industry, vol. 147, p. 103876, 2023.
- M. L. Caterina Agrimonti and G. Visioli, “Smart agriculture for food quality: facing climate change in the 21st century,” Critical Reviews in Food Science and Nutrition, vol. 61, no. 6, pp. 971–981, 2021.
- A. De Salve, A. Lisi, P. Mori, L. Ricci, and C. Turco, “Self-Sovereign Identity for Privacy-Preserving Shipping Verification System,” in Proceedings of the 2022 5th International Conference on Blockchain Technology and Applications, ser. ICBTA ’22. New York, NY, USA: Association for Computing Machinery, 2023, p. 147–157.
- J. Li, Q. He, R. Liang, and B. Jiang, “Smart Tourism Identity Authentication Service Based on BlockChain and Decentralized Identifier,” in Blockchain and Trustworthy Systems, H.-N. Dai, X. Liu, D. X. Luo, J. Xiao, and X. Chen, Eds. Singapore: Springer Singapore, 2021, pp. 545–558.
- M. Y. Başer, T. Büyükbeşe, and M. Kizildag, “What if we could travel without passport? First sight to blockchain-based identity management in tourism,” Asia Pacific Journal of Tourism Research, vol. 28, no. 4, pp. 341–363, 2023.
- E. Wolz, M. Gottlieb, and H. Pongratz, “Digital Credentials in Higher Education Institutions: A Literature Review,” in Innovation Through Information Systems, F. Ahlemann, R. Schütte, and S. Stieglitz, Eds. Cham: Springer International Publishing, 2021, pp. 125–140.
- R. Q. Saramago, L. Jehl, H. Meling, and V. Estrada-Galiñanes, “A Tree-based Construction for Verifiable Diplomas with Issuer Transparency,” in 2021 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), 2021, pp. 101–110.
- D. Serranito, A. Vasconcelos, S. Guerreiro, and M. Correia, “Blockchain Ecosystem for Verifiable Qualifications,” in 2020 2nd Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS), 2020, pp. 192–199.
- E. Tan, E. Lerouge, J. Du Caju, and D. Du Seuil, “Verification of Education Credentials on European Blockchain Services Infrastructure (EBSI): Action Research in a Cross-Border Use Case between Belgium and Italy,” Big Data and Cognitive Computing, vol. 7, no. 2, 2023.
- P. Herbke and H. Yildiz, “ELMO2EDS: Transforming Educational Credentials into Self-Sovereign Identity Paradigm,” in 2022 20th International Conference on Information Technology Based Higher Education and Training (ITHET), 2022, pp. 1–7.
- N. Fotiou, V. A. Siris, G. C. Polyzos, Y. Kortesniemi, and D. Lagutin, “Capabilities-based access control for IoT devices using Verifiable Credentials,” in 2022 IEEE Security and Privacy Workshops (SPW), 2022, pp. 222–228.
- . Doğan and H. Karacan, “A Blockchain-Based E-Commerce Reputation System Built With Verifiable Credentials,” IEEE Access, vol. 11, pp. 47 080–47 097, 2023.
- Z. Pervez, Z. Khan, A. Ghafoor, and K. Soomro, “SIGNED: Smart cIty diGital twiN vErifiable Data Framework,” IEEE Access, vol. 11, pp. 29 430–29 446, 2023.
- A. Sabbioni, T. Villano, and A. Corradi, “An Architecture for Service Integration to Fully Support Novel Personalized Smart Tourism Offerings,” Sensors, vol. 22, no. 4, 2022.
- H. Chen, “This world-class airport will soon go passport-free,” Cable News Network (CNN). [Online]. Available: https://edition.cnn.com/travel/article/changi-airport-singapore-passport-free-travel-intl-hnk/index.html
- B.-C. Chifor, I. Bica, V.-V. Patriciu, and F. Pop, “A security authorization scheme for smart home Internet of Things devices,” Future Generation Computer Systems, vol. 86, pp. 740–749, 2018.
- A. De Benedictis, N. Mazzocca, A. Somma, and C. Strigaro, “Digital Twins in Healthcare: An Architectural Proposal and Its Application in a Social Distancing Case Study,” IEEE Journal of Biomedical and Health Informatics, vol. 27, no. 10, pp. 5143–5154, 2023.
- S. West, O. Stoll, J. Meierhofer, and S. Züst, “Digital Twin Providing New Opportunities for Value Co-Creation through Supporting Decision-Making,” Applied Sciences, vol. 11, no. 9, 2021.
- D. Maram, H. Malvai, F. Zhang, N. Jean-Louis, A. Frolov, T. Kell, T. Lobban, C. Moy, A. Juels, and A. Miller, “CanDID: Can-Do Decentralized Identity with Legacy Compatibility, Sybil-Resistance, and Accountability,” in 2021 IEEE Symposium on Security and Privacy (SP), 2021, pp. 1348–1366.
- R. Chen, F. Shu, S. Huang, L. Huang, H. Liu, J. Liu, and K. Lei, “BIdM: A Blockchain-Enabled Cross-Domain Identity Management System,” Journal of Communications and Information Networks, vol. 6, no. 1, pp. 44–58, 2021.
- J. Yin, Y. Xiao, Q. Pei, Y. Ju, L. Liu, M. Xiao, and C. Wu, “SmartDID: A Novel Privacy-Preserving Identity Based on Blockchain for IoT,” IEEE Internet of Things Journal, vol. 10, no. 8, pp. 6718–6732, 2023.
- R. Belchior, B. Putz, G. Pernul, M. Correia, A. Vasconcelos, and S. Guerreiro, “SSIBAC: Self-Sovereign Identity Based Access Control,” in 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), 2020, pp. 1935–1943.
- V. Bolgouras, A. Angelogianni, I. Politis, and C. Xenakis, “Trusted and Secure Self-Sovereign Identity Framework,” in Proceedings of the 17th International Conference on Availability, Reliability and Security, ser. ARES ’22. New York, NY, USA: Association for Computing Machinery, 2022.
- N. Fotiou, V. A. Siris, and G. C. Polyzos, “Enabling self-verifiable mutable content items in IPFS using Decentralized Identifiers,” in 2021 IFIP Networking Conference (IFIP Networking), 2021, pp. 1–6.
- C. Farmer, S. Pick, and A. Hill, “Decentralized identifiers for peer-to-peer service discovery,” in 2021 IFIP Networking Conference (IFIP Networking), 2021, pp. 1–6.
- T. Zhong, P. Shi, and J. Chang, “Jointcloud cross-chain verification model of decentralized identifiers,” in 2021 IEEE International Performance, Computing, and Communications Conference (IPCCC), 2021, pp. 1–8.
- N. Fotiou, Y. Thomas, V. A. Siris, G. Xylomenos, and G. C. Polyzos, “Securing Named Data Networking routing using Decentralized Identifiers,” in 2021 IEEE 22nd International Conference on High Performance Switching and Routing (HPSR), 2021, pp. 1–6.
- A. Sharif, M. Ranzi, R. Carbone, G. Sciarretta, F. A. Marino, and S. Ranise, “The eIDAS Regulation: A Survey of Technological Trends for European Electronic Identity Schemes,” Applied Sciences, vol. 12, no. 24, 2022.
- European Union, “Regulation (EU) No 910/2014 of the European Parliament and of the Council of 23 July 2014 on Electronic Identification and Trust Services for Electronic Transactions in the Internal Market and Repealing Directive 1999/93/EC,” 2014. [Online]. Available: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=uriserv:OJ.L_.2014.257.01.0073.01.ENG
- B. Podgorelec, L. Alber, and T. Zefferer, “What is a (Digital) Identity Wallet? A Systematic Literature Review,” in 2022 IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC), 2022, pp. 809–818.
- European Union, “ European Self-Sovereign Identity Framework Lab.” [Online]. Available: https://essif-lab.eu/
- European Commission, “ Regulation of the European Parliament and of The Council Amending Regulation (Eu) No 910/2014 as Regards Establishing a Framework for a European Digital Identity.” [Online]. Available: https://ec.europa.eu/digital-building-blocks/wikis/display/EBSI/Home
- Decentralized Identity, “ European Digital Identity and SSI.” [Online]. Available: https://decentralized-id.com/government/europe/#regional
- J. Li and Y. Jing, “Establishing an International Engagement Model of Digital Identity Based on Blockchain,” Mobile Information Systems, vol. 2022, p. 6988211, Aug 2022.
- O. Avellaneda, A. Bachmann, A. Barbir, J. Brenan, P. Dingle, K. H. Duffy, E. Maler, D. Reed, and M. Sporny, “Decentralized Identity: Where Did It Come From and Where Is It Going?” IEEE Communications Standards Magazine, vol. 3, no. 4, pp. 10–13, 2019.
- J. Li and Y. Jing, “Establishing an International Engagement Model of Digital Identity Based on Blockchain,” Mobile Information Systems, vol. 2022, 2022.
- U.S. Department of Homeland Security, “ News Release: DHS S&T Seeks Solutions for Privacy Preserving Digital Credential Wallets & Verifiers ,” 2023. [Online]. Available: https://www.dhs.gov/science-and-technology/news/2023/06/22/st-seeks-solutions-privacy-preserving-digital-credential-wallets-verifiers
- Digital Identity and Authentication Council of Canada, “ Perspectives on the Adoption of Verifiable Credentials ,” 2023. [Online]. Available: https://diacc.ca/2023/05/09/perspectives-on-the-adoption-of-verifiable-credentials/
- J. Sedlmeir, R. Smethurst, A. Rieger, and G. Fridgen, “Digital identities and verifiable credentials,” Business & Information Systems Engineering, vol. 63, no. 5, pp. 603–613, 2021.
- “Identidad Digital para la Inclusión.” [Online]. Available: https://didi.org.ar/en/
- “Farmer Connect.” [Online]. Available: https://www.farmerconnect.com/
- S. Nadhamuni, “The Future of Digital Identity Verification: In the era of AI Deep Fakes,” 2023. [Online]. Available: https://curator.artracx.com/
- S. Kim, A. Zhang, R. Liao, W. Zheng, Z. Hu, and Z. Sun, “Sampling blockchain-enabled smart city applications among South Korea, the United States and China,” Journal of Smart Cities and Society, vol. 1, no. 1, pp. 53–70, 2022.
- “China introduces identity verification through RealDID on blockchain.” [Online]. Available: https://medium.com/@coinness.gl/china-introduces-identity-verification-through-realdid-on-blockchain-57a30c4adbd6
- WeBank, “ WeIdentity.” [Online]. Available: https://weidentity.readthedocs.io/en/latest/README.html
- “ Artracx Curator.” [Online]. Available: https://curator.artracx.com/
- “Taiwan DID.” [Online]. Available: https://github.com/tw-did/tw-did
- Dock Network, “ Gravity case study .” [Online]. Available: https://www.dock.io/gravity-case-study
- Diwala , “ Diwala .” [Online]. Available: https://www.diwala.io/
- “Case Study: Kiva launches Africa’s first national decentralized ID system with Hyperledger Indy,” 2021. [Online]. Available: https://www.hyperledger.org/wp-content/uploads/2021/01/Hyperledger_CaseStudy_Kiva_Printable.pdf
- M. Freytsis, I. Barclay, S. K. Radha, A. Czajka, G. H. Siwo, I. Taylor, and S. Bucher, “Development of a mobile, self-sovereign identity approach for facility birth registration in Kenya,” Frontiers in Blockchain, vol. 4, p. 631341, 2021.
- Z. Ziyi Li, K. L. Joseph, J. Yu, and D. Gasevic, “Blockchain-based Solutions for Education Credentialing System: Comparison and Implications for Future Development,” in 2022 IEEE International Conference on Blockchain (Blockchain), 2022, pp. 79–86.
- J. Soong, “ 2023 the break out year for Digital Identity — June Newsletter ,” 2023. [Online]. Available: https://digitalidentity.nz/2023/06/21/2023-the-break-out-year-for-digital-identity-june-newsletter/
- C. International, “ The Credentials Verification Service for the Nursing Council of New Zealand .” [Online]. Available: https://ncnz.cgfns.org/
- F. Hoops, A. Mühle, F. Matthes, and C. Meinel, “A Taxonomy of Decentralized Identifier Methods for Practitioners,” in 2023 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), 2023, pp. 57–65.
- F. Zhang, E. Cecchetti, K. Croman, A. Juels, and E. Shi, “Town Crier: An Authenticated Data Feed for Smart Contracts,” in Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, ser. CCS ’16. New York, NY, USA: Association for Computing Machinery, 2016, p. 270–282.
- F. Zhang, D. Maram, H. Malvai, S. Goldfeder, and A. Juels, “DECO: Liberating Web Data Using Decentralized Oracles for TLS,” in Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, ser. CCS ’20. New York, NY, USA: Association for Computing Machinery, 2020, p. 1919–1938.
- M. Korir, S. Parkin, and P. Dunphy, “An Empirical Study of a Decentralized Identity Wallet: Usability, Security, and Perspectives on User Control,” in Eighteenth Symposium on Usable Privacy and Security (SOUPS 2022). Boston, MA: USENIX Association, Aug. 2022, pp. 195–211. [Online]. Available: https://www.usenix.org/conference/soups2022/presentation/korir
- J. Sedlmeir, R. Smethurst, A. Rieger, and G. Fridgen, “Digital Identities and Verifiable Credentials,” Business & Information Systems Engineering, vol. 63, no. 5, pp. 603–613, Oct 2021.
- Z. E. Ansaroudi, R. Carbone, G. Sciarretta, and S. Ranise, “Control is Nothing Without Trust a First Look into Digital Identity Wallet Trends”,” in Data and Applications Security and Privacy XXXVII, V. Atluri and A. L. Ferrara, Eds. Cham: Springer Nature Switzerland, 2023, pp. 113–132.
- A. Shankar, P. Pandiaraja, K. Sumathi, T. Stephan, and P. Sharma, “Privacy preserving E-voting cloud system based on ID based encryption,” Peer-to-Peer Networking and Applications, vol. 14, no. 4, pp. 2399–2409, Jul 2021.
- M. Sallal, R. de Fréin, and A. Malik, “PVPBC: Privacy and Verifiability Preserving E-Voting Based on Permissioned Blockchain,” Future Internet, vol. 15, no. 4, 2023.
- S. Mihai, M. Yaqoob, D. V. Hung, W. Davis, P. Towakel, M. Raza, M. Karamanoglu, B. Barn, D. Shetve, R. V. Prasad, H. Venkataraman, R. Trestian, and H. X. Nguyen, “Digital Twins: A Survey on Enabling Technologies, Challenges, Trends and Future Prospects,” IEEE Communications Surveys & Tutorials, vol. 24, no. 4, pp. 2255–2291, 2022.
- A. Farao, E. Veroni, C. Ntantogian, and C. Xenakis, “P4G2Go: A Privacy-Preserving Scheme for Roaming Energy Consumers of the Smart Grid-to-Go,” Sensors, vol. 21, no. 8, 2021.
- M.-H. Rhie, K.-H. Kim, D. Hwang, and K.-H. Kim, “Vulnerability Analysis of DID Document’s Updating Process in the Decentralized Identifier Systems,” in 2021 International Conference on Information Networking (ICOIN), 2021, pp. 517–520.
- C.-S. Park and H.-M. Nam, “A New Approach to Constructing Decentralized Identifier for Secure and Flexible Key Rotation,” IEEE Internet of Things Journal, vol. 9, no. 13, pp. 10 610–10 624, 2022.
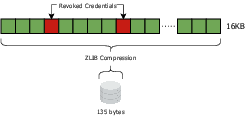
- W. Recommendation, “Revocation List 2020,” 2021. [Online]. Available: https://w3c-ccg.github.io/vc-status-rl-2020/
- J.-l. Gailly and M. Adler, “Zlib compression library,” 2004.
- R. R. Mullins, M. Ahearne, S. K. Lam, Z. R. Hall, and J. P. Boichuk, “Know Your Customer: How Salesperson Perceptions of Customer Relationship Quality Form and Influence Account Profitability,” Journal of Marketing, vol. 78, no. 6, pp. 38–58, 2014.
- A. K. Shaikh, M. Al-Shamli, and A. Nazir, “Designing a relational model to identify relationships between suspicious customers in anti-money laundering (aml) using social network analysis (sna),” Journal of Big Data, vol. 8, no. 1, p. 20, Jan 2021.
Paper Prompts
Sign up for free to create and run prompts on this paper using GPT-5.
Top Community Prompts
Collections
Sign up for free to add this paper to one or more collections.